Networking Configurations Supported By AWS Cloud Provider
This tutorial describes the various networking configurations Platform9 Managed Kubernetes supports on Amazon AWS.
Platform9 Managed Kubernetes provides a native integration with various Cloud Providers including Amazon AWS, where it utilizes native capabilities provided by the cloud for networking and storage integrations during creation of Kubernetes clusters on these endpoints.
A key component of this process is integration with different networking configurations on AWS.
Following are the 4 different networking configurations that we support today. If you would like to see support for an additional configuration, drop us a note to support@platform9.com.
Creation of New VPC Using Public Subnet(s)
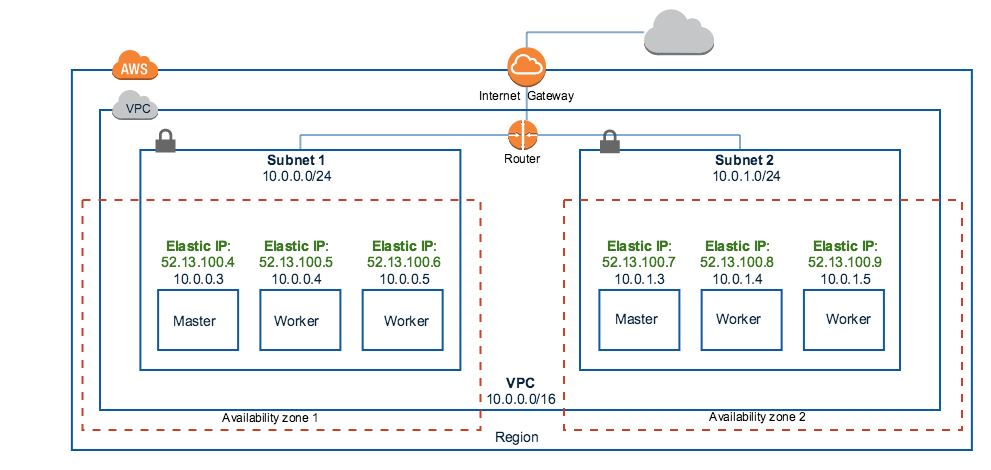
This is the default and the simplest option while creating Kubernetes clusters on Amazon AWS. With this option, Platform9 creates the following on your AWS endpoint ;
- A new AWS VPC in your chosen region. This will internally create a router and an internet gateway to map your private subnets to the internet
- A new public subnet per availability zone you’ve selected for the cluster
- Route table entries in the router created above to enable this configuration
- Elastic IP per node in the Kubernetes cluster being created
Each node in this cluster configuration is thus routable from the internet and gets its own public IP.
Once created, the cluster nodes are easily accessible from the internet for debugging purpose.
NOTE: While this is the easiest configuration for testing Managed Kubernetes, it’s also the most unsecure option as all your nodes are publicly accessible. We do not recommend this configuration for production workloads.
Creation of New VPC Using Private Subnet(s)
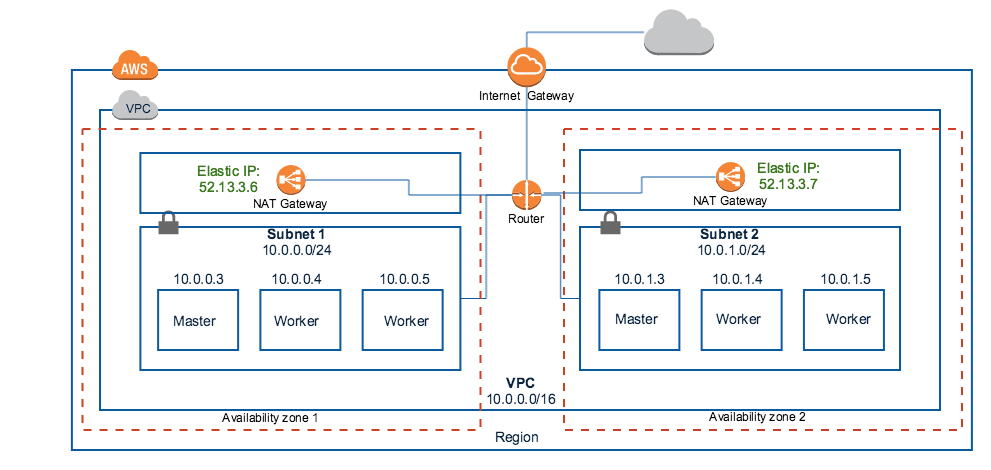
With this option, Platform9 creates the following on your AWS endpoint:
- A new AWS VPC in your chosen region. This will internally create a router and an internet gateway to map your private subnets to the internet
- A new private subnet per avaibility zone you’ve selected for the cluster
- A NAT gateway per availability zone to map the private subnet to internet with an elastic IP address
- Route table entries in the router to enable this configuration
This option is more secure than the previous option and is recommended for production workloads.
The cluster nodes are accessible from within the cluster only but not from outside. The nodes can reach the internet via the NAT gateway but they are not reachable externally.
Integration with an Existing VPC
If you have existing VPC setup that is configured per your organization’s requirements and you’d like to utilize that for Managed Kubernetes deployment, this option allows you to do that.
With this option, Platform9 will not create any networking components behind the scene, it will utilize existing networking configuration you have. In addition to selecting an existing VPC, you are asked to select a (public or private) subnet per Availability zone where the cluster nodes are to be deployed.
This option allows you to seamlessly integrate Managed Kubernetes in your existing setup.
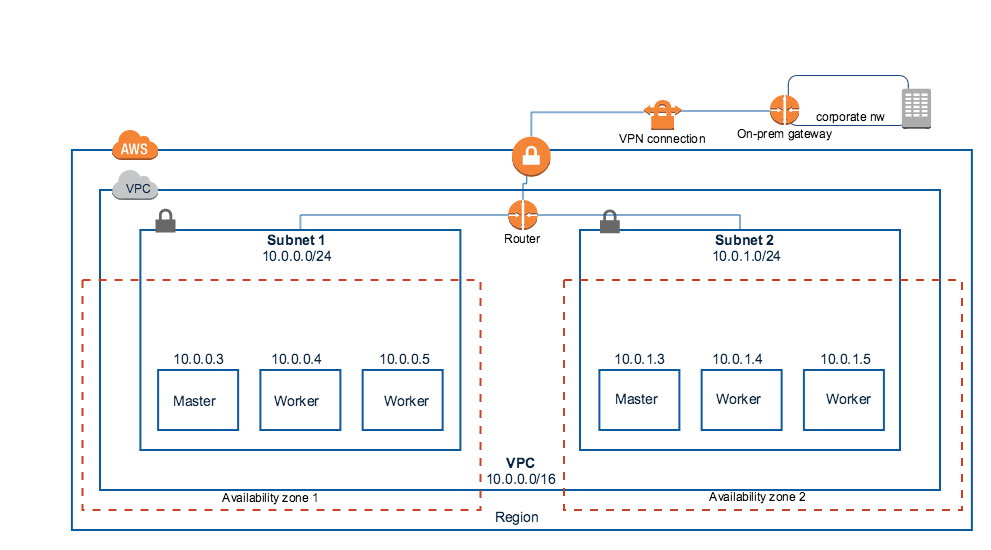
Integration with an Existing VPN Setup Within AWS
Large enterprises will typically have VPN configured to enable direct connect access to their corporate data center environment. Platform9 Managed Kuberntes can integrate with this setup. When you select this option, Managed Kubernetes does not create any networking component in your AWS environment. It simply integrates with your existing VPN setup. If you choose this option, you will likely need to specify your organization’s network proxy as part of the wizard so that traffic can be routed appropriately.
Note: It is not possible to utilize a DNS lookup to access remote servers over a VPN from an Amazon VPC. Refer to the article Accessing Remote Servers over VPN from Amazon Virtual Private Cloud for details.
Refer to the article Setting up Kubernetes Clusters on Amazon VPC based Private Subnets to understand behind-the-scene details of what gets configured.