How Platform9 Enables Operational Security
Introduction
Platform9 delivers a SaaS managed open source based cloud service that enables enterprises to transform their existing data center infrastructure into an agile, self-service private cloud. In addition to being easy and efficient, Platform9 places major emphasis on ensuring operational security when delivering open source cloud frameworks like OpenStack and Kubernetes in a SaaS managed fashion. Platform9’s solutions are designed to keep enterprise infrastructure and workloads secure. The information below details the security measures we’ve designed within our infrastructure and product, as well as options available to administrators, that allows Platform9 to function as a secure platform to manage your infrastructure.
Platform9 Product Security
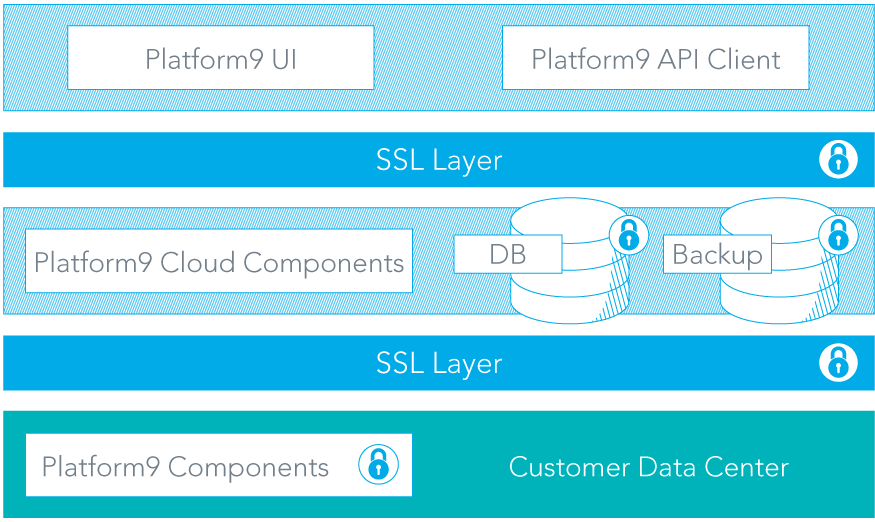
Below is a diagram which describes high-level Platform9 architecture, highlighting various components.
- Single sign on (SAML) Support: Platform9 supports integration with SAML identity providers, helping enterprises have a single login policy (like MFA token, password length) across all applications. It also alleviates the need for adding/updating/removing individual users on Platform9 portal.
- MFA (TOTP) support: Even though SAML integration with a dedicated identity provider is recommended, Platform9 supports use of TOTP (time-based one-time password) if a customer decides not to use SAML integration.
- SSL with client-side authentication: Mutual authentication for communication with agent software. Each deployment unit has its own unique, self-signed root certificate authority. This certificate authority is used to generate 2048-bit keys that are in turn used to secure all communications between the deployment unit and agent software that interacts with it using SSL encryption. Both the deployment unit, and any agent software (including host agent and OpenStack/Kubernetes agent software) use these keys to mutually authenticate via https. This prevents any agent software configured for a different customer from mistakenly or maliciously accessing the deployment unit.
- SSL for API and UI client: GeoTrust signed certificates for API clients. The services hosted by the deployment unit are accessed using REST APIs by the Clarity user interface or customer developed automation. These clients can authenticate the server by using GeoTrust signed certificates. The server authenticates the client with Keystone, the role-based identity service used by OpenStack or Kubernetes built in RBAC capabilities.
- Code signing: Platform9 host-side software upgrades and installs additional component on premises on upgrade schedule and host re-configuration actions by users. These software packages are ‘signed’ by Platform9.
- Restricted access user: Platform9 on-premises component run as user “pf9” group“pf9group.” The set of sudo privileges required by user pf9 can be obtained from Platform9 on request and can be used to further restrict access to the actions Platform9 can perform.
- Metadata only: Platform9 deployment units only receive metadata from agent software, such as host hardware configuration, software packages information, relevant log files from the host, and virtual machine identifier and configuration. Deployment units do not receive data from running or offline virtual machines, or any other data from hosts.
- No need to open ports: The deployment unit or any software therein doesn’t initiate a network session into any customer hosts. Authorized agents that are installed on hosts initiate necessary calls to the deployment unit using outbound, https connections. No new ports to open limits the attack surface area.
- Roles and privileges: Administrators can limit access and, therefore, the security surface of the system by using pre-configured roles that have reduced privileges. For instance, most users of the system would be configured with the ‘self-service user’ role, which doesn’t allow them to perform protected operations on virtual machine instances that they do not own.
Platform9 Operational Security
- Isolated customers: No shared multi-tenancy across customers. No two customers of Platform9 share a deployment unit.
- Virtual firewall: Customers can restrict access to the deployment unit by specifying the IP settings of one or more allowable source networks.
- Monthly updates: Deployment units are patched for security updates regularly. Updates are pushed monthly to include the latest security patches. Critical vulnerabilities are addressed and patched immediately.
- Encryption at rest: Platform9 performs regular backups and all backups are encrypted.
- Physical security: Platform9’s server equipment is secured in a level 3 datacenter and keys are only provided to authorized employees. Employees develop their software using computers with strong passwords and encrypted disk storage in case of loss or theft.
- Data centers: Platform9 uses a well-known public cloud computing service provider to host customer production environments. These environments are configured for multi- geographical availability in case of a disaster or other outage in any specific geography.
- Incident response: If despite all other protection in place, customer data is accessed without authorization, Platform9 will notify you. If personal information about customers is breached from Platform9, we will notify customers in accordance with California Law (California Civil Code Section 1798.29 and Section 1798.82).
Privacy
Guiding user’s privacy and that of their business data is something we take seriously, and we work hard to protect user information from unauthorized access. Our privacy policy is available along with our terms and conditions.
Summary
Platform9 helps enterprises manage their infrastructure as an agile, self-service, secure private cloud. To learn more about Platform9 and how it could add value to your business, please reach out to us at customer-success@platform9.com.