Why Calico?
We want to ensure we provide the best Kubernetes software-defined networking experience that is possible with an emphasis on supporting encryption, security policies, BGP, a fast data plane and can also be deployed consistently across private, edge, and public clouds.
Last year we had a request from a customer to support Calico using external peering to their F5. This meant configuring Calico in its native, non-encapsulated, no NAT; BGP. Why? Simply put, performance. Flannel’s encapsulation and traversing their network was slowing down their response times and in turn, was impacting their public-facing applications. By using BGP they would be able to provide networking directly to Pods and Services, reducing network complexity and improving end-user performance.
While our solutions architecture team reviewed their request, we kicked off a review of the CNI landscape to assess if we could consolidate to a single CNI. What we found was that although many CNI plugins offer similar capabilities, only Calico provided the portability and consistent operations across all clouds that are central to Platform9, and also maintained performance and security requirements.
Performance across CNI plugins is fairly stable, impacted primarily by MTU settings, and the configured Kubernetes data plane, (IPTables vs IPVS vs eBPF). However, when performance is reviewed in context to encryption the landscape changes. The team at ITNEXT benchmarked a few CNI offerings, including Flannel, Weave Net, Cilium, and Calico, and documented the results. In their latest update, they pulled in data across the CNIs that support encryption for Calico which means enabling Wire Guard. The results? Calico provided over twice the throughput of the next closest competitor.
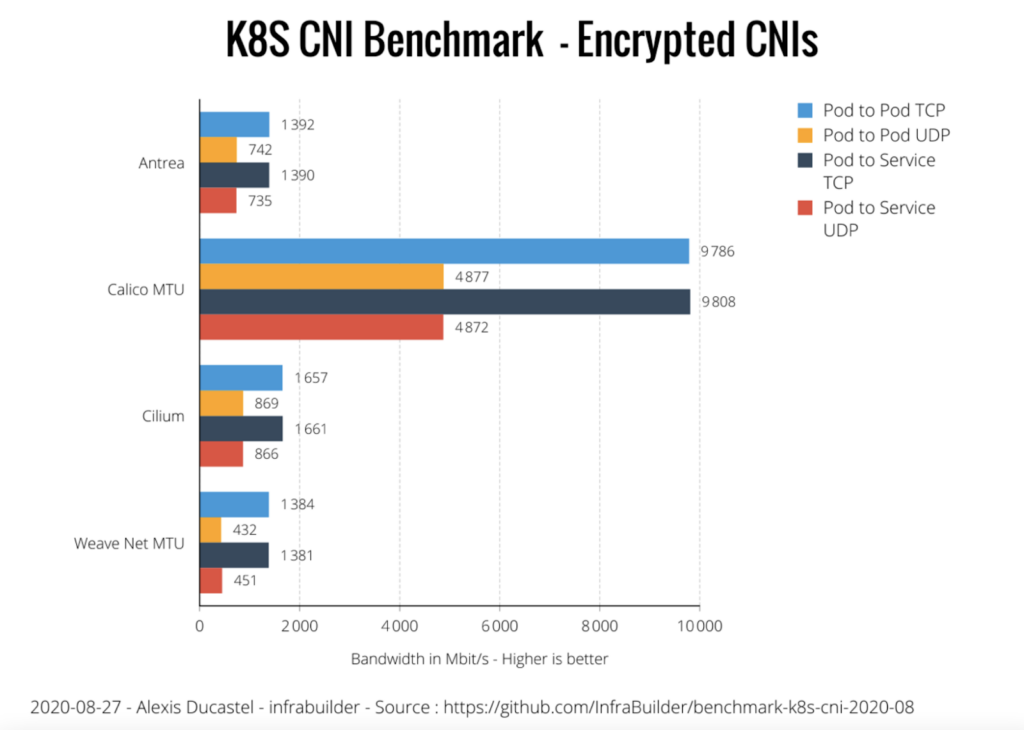
If you’re interested, the full benchmark can be found here.
Ultimately, we decided that as a managed provider we need to provide a holistic SDN service that is comparable with our Managed OpenStack platform.
Software-defined networking is nothing new to Platform9. Our team has been supporting customer’s SDN needs for the last 6 years. This request, however, was an ask that encompassed an entirely new stack and posed a much more significant question: wherein the Kubernetes networking stack do we as a SaaS Managed provider with a 99.9% uptime SLA, start and stop.
CNI as a Software-Defined Network
As the product manager, it was critical to understand the entirety of the question at hand. With our Managed OpenStack, for example, it is clear–we provide Neutron, we support Neutron including all of its features, performance, and availability. For Kubernetes, our users have had a choice: Flannel or Calico. Users could choose their CNI as intended by the Kubernetes community. This means that as a SaaS Managed provider, we drew the line at Kubernetes support. We could help, but we didn’t commit 99.9% SLA on each and every CNI. So the question, where does our support start and stop for Calico as an SDN means changing the approach.
Why Calico and not the many other CNIs?
The answer: Open-source, completeness, market presence, and enterprise support. First, it must be open-source, otherwise, we are failing to deliver on our mission, ‘to make open-source easy and available to everyone.’ Completeness; Calico supports VXLAN, NAT, external peering, wire guard, multiple AS’s, and rout-reflector configurations, all in addition to a very functional security policy implementation. These factors drove the decision to consolidate our CNI offering and expand our responsibilities.
Why Managed Calico?
When we first launched Platform9 Managed Kubernetes in 2017, the Container Network Interface and Kubernetes were both in very different places. Many of the features today didn’t exist or were in alpha, and 99% of Kubernetes users were all still learning how to install a cluster–let alone trying to figure out the tradeoffs of different networking options. The same goes for Calico. Over the last 3 years, we supported Flannel as our primary CNI–it was simple, caused few issues, met the requirements of our customers, and continues to do so. However, Calico exceeds expectations across the board, and as a SaaS Managed provider that guarantees a 99.9% uptime, Calico is the clear market leader and choice as an enterprise-ready, scalable, and secure CNI.
With the Platform9 release of 5.0, we have officially graduated Calico as our preferred Kubernetes CNI– software-defined network of choice, with fully managed support for all configurations across clusters in AWS and importantly, private and edge locations running physical servers or virtual machines. That’s 99.9% uptime, managed deployment, managed upgrades, solution architecture help, and 24/7 support.
Platform9 Managed Calico
We manage your clusters, OS upwards–unless you’re using Platform9 Managed Bare Metal, then we manage the bare metal too. This means we start where the Calico software-defined network starts, and stop where your cluster’s infrastructure connects to your supporting network. On-premises means we help connect Calico to your network, including external BGP peering. The switch infrastructure remains in your control.
Additionally, we assist you through troubleshooting Calico connectivity issues and manage the lifecycle and upgrades.
We want to ensure that your Kubernetes experience is the best possible, and the network is a critical piece.
One last thing: Platform9’s Calico API
Calico is great, however, the only way to interact with it is via the CalicoCtl — the command line interface. To manage Calico we needed to fix this, so we built an API enabling our SaaS Management Plane to orchestrate Calico across all of your clusters, public, private and edge clouds.
Moving forward we will be expanding our Calico capabilities to include Security Policy Management from our SaaS management plane. This means more robust web application visualization and control policies, templated cluster configurations, and a full user interface for configuring, updating, and changing Calico in your clusters.