Edit RBAC Profiles
Edit Profile
If you need to modify an RBAC profile, you can select it using the radio button and then use one of the three icons above the profile name, which becomes available to use. The three options are as follows.
- Manage Bindings
- Edit
- Delete
Using the edit function, we can return to the menu and choose one of the four tabs (Roles, ClusterRoles, RoleBindings, and ClusterRoleBindings). We then modify its settings in the RBAC Profile, where we can also see the available namespaces.
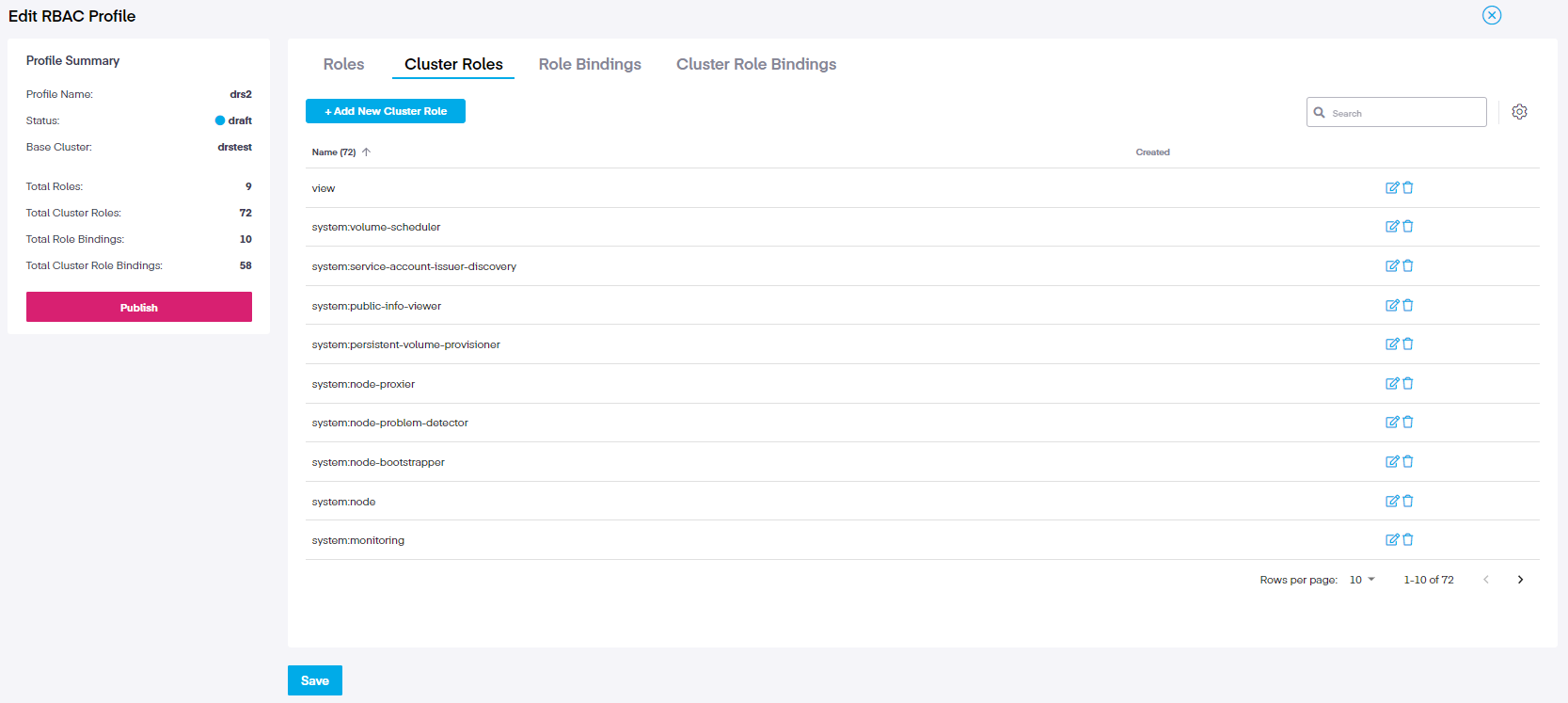
For example, if we choose the ClusterRole tab and the click on the small edit icon to the right of each role, it opens a new window which allows further editing of the resources, which will search the linked cluster and show any additional verbs that may not be included in the policy.
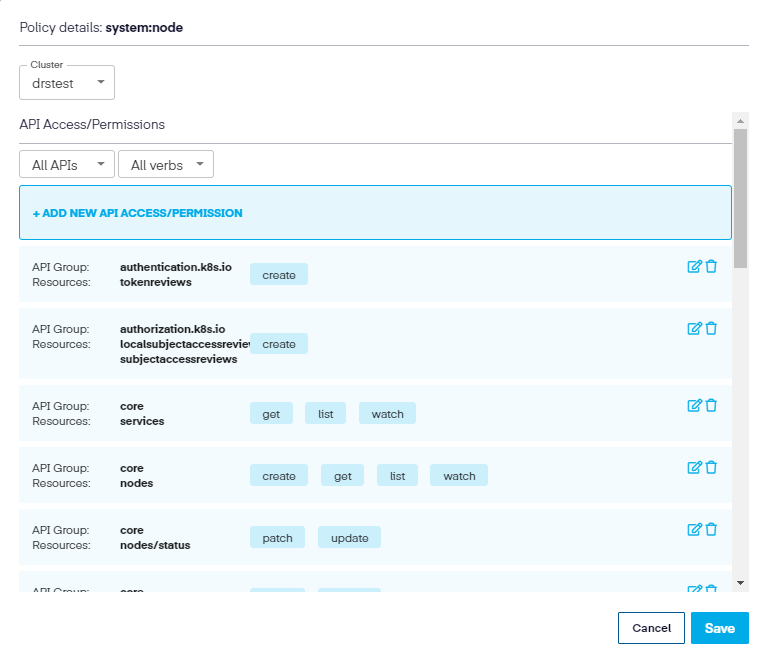
You can then modify the resource further by clicking the Edit icon to the right and add any auxiliary verbs needed to the resource.
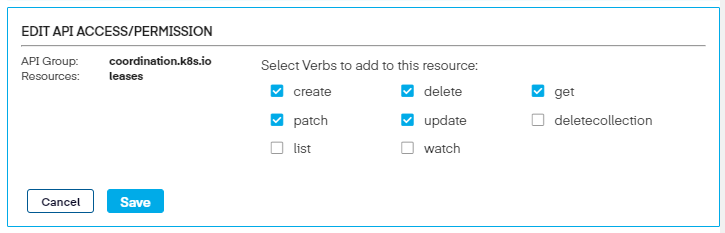
Lastly, click Save three times to updates the policy, and brings us back to the edit screen.
Add Roles
In the Edit RBAC Profile screen, we can also add additional Roles, ClusterRoles, RoleBindings, and ClusterRoleBindings to existing profiles. To accomplish this, select the tab to choose the role to update and then click on (in this example) the Add New Cluster Role.
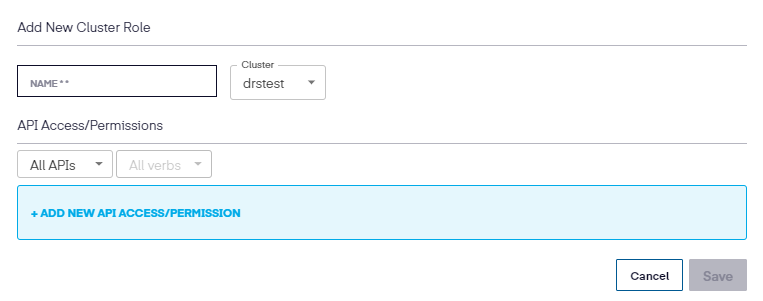
Next, add the name, select the cluster, and then the new API Access/Permission.
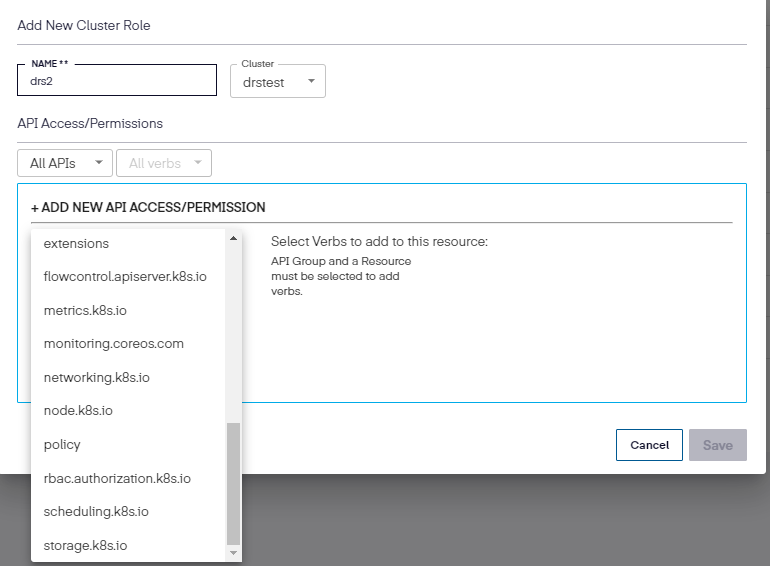
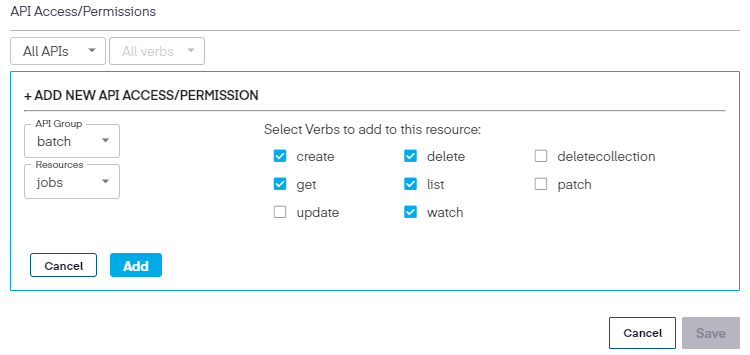
Once the API Group and resource is chosen, select the permissions to be used.
Once completed, click Add, then Save to update the New Cluster Role.
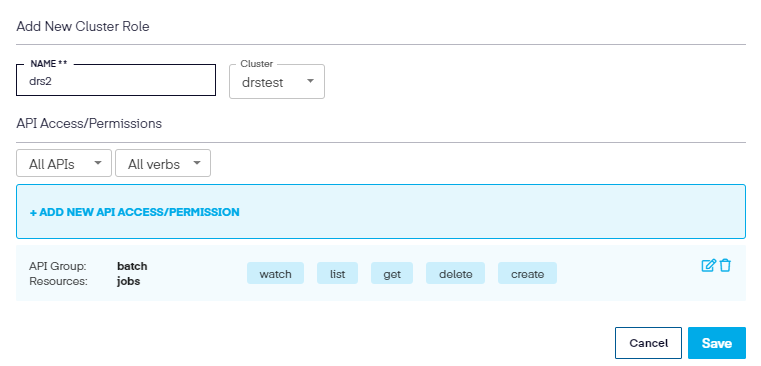
When returned to the edit screen, click Save again to complete the modification.
To add an RBAC Policy without an existing cluster use the YAML view of the Add Role, Cluster Role or Role Bindings of Cluster Role Bindings
Permission Types Quick View
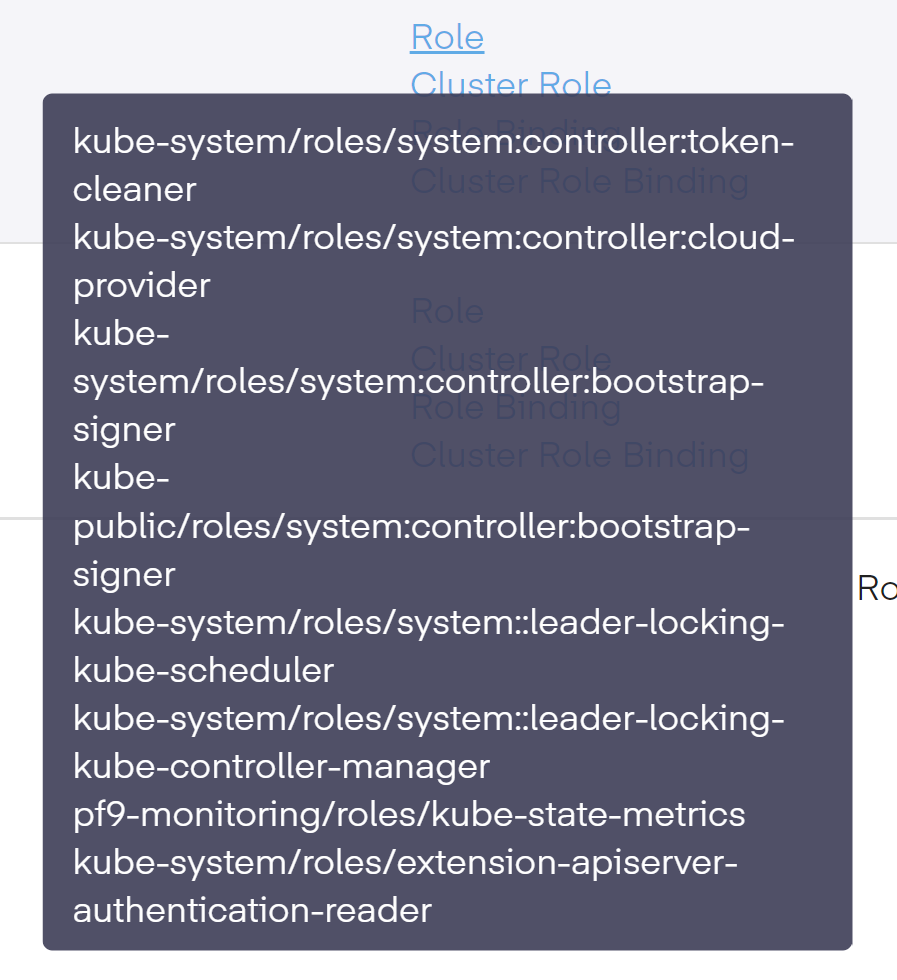
As an additional element, once back in the main RBAC Profile screen, we can review the different permissions for the Roles, ClusterRoles, RoleBindings, and ClusterRoleBindings types by momentarily hovering our mouse over each role.
This shows us the currently assigned permissions of each role.