Enabling SSO and SAML Groups in PMK
Introduction
In this article, we describe the features included in the UI, which allow administrators to enable single-sign-on using Groups and User mappings.
These features are under the Enterprise SSO dashboard in the Admin Settings. With this solution, users can create a named group, assign them access to a specific tenant and region access as Admin, Self Service or Read only.
To access these settings, click on the username in the upper-right hand corner, then click on Admin Settings.
SSO
Once in the Admin Settings area, we can go to the Enterprise SSO tab to view and edit the SSO (Enterprise Single Sign On) and the SAML Groups tabs.
Initially, the Enable SSO slide selector will be toggled to the off position. Slide selector right to enable this feature.
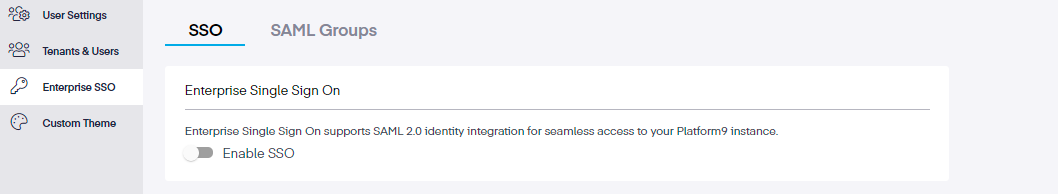
If you receive a popup stating asking you to upgrade your account, reach out to our Support Team for further assistance.
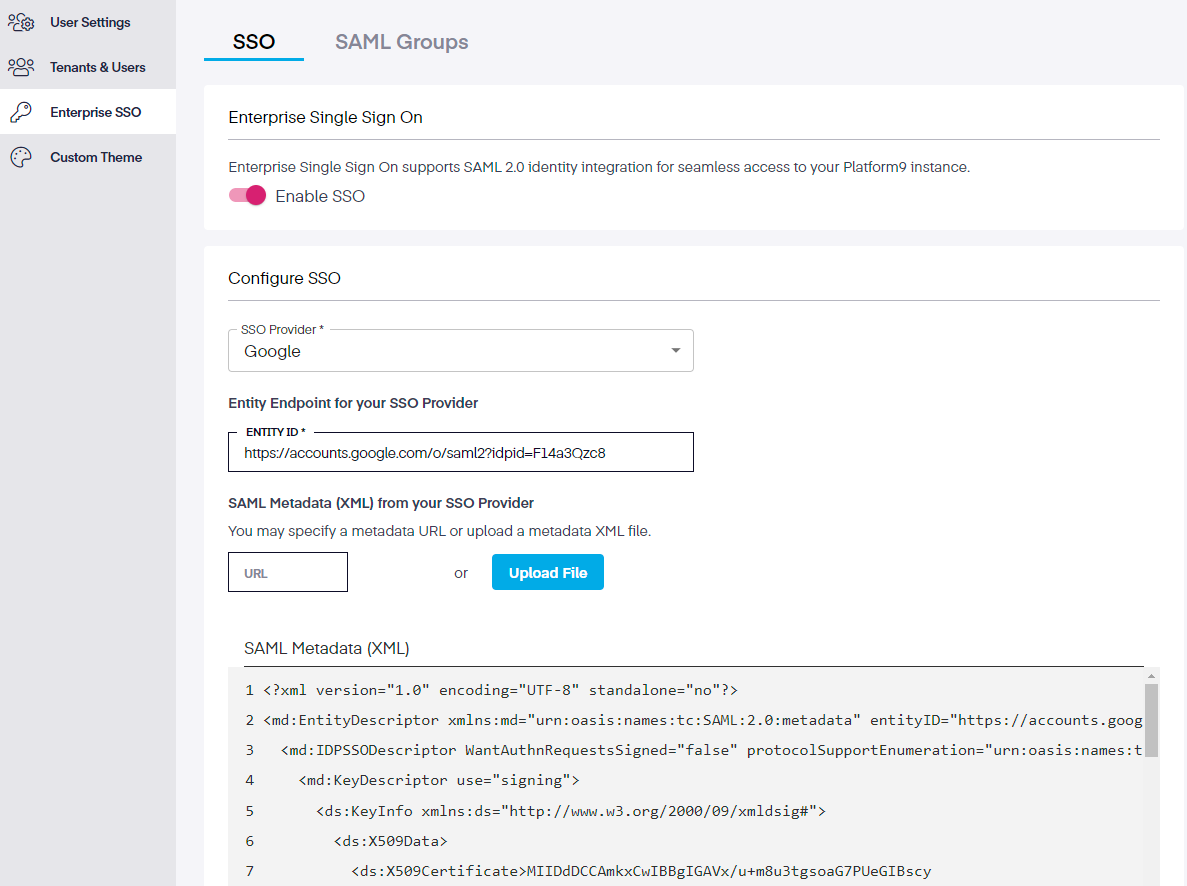
Once SSO has been enabled, select the SSO provider you wish to use. We have picked Google as our choice.

Next, enter in your Entity ID, the SAML Metadata and any other relevant material, then click the
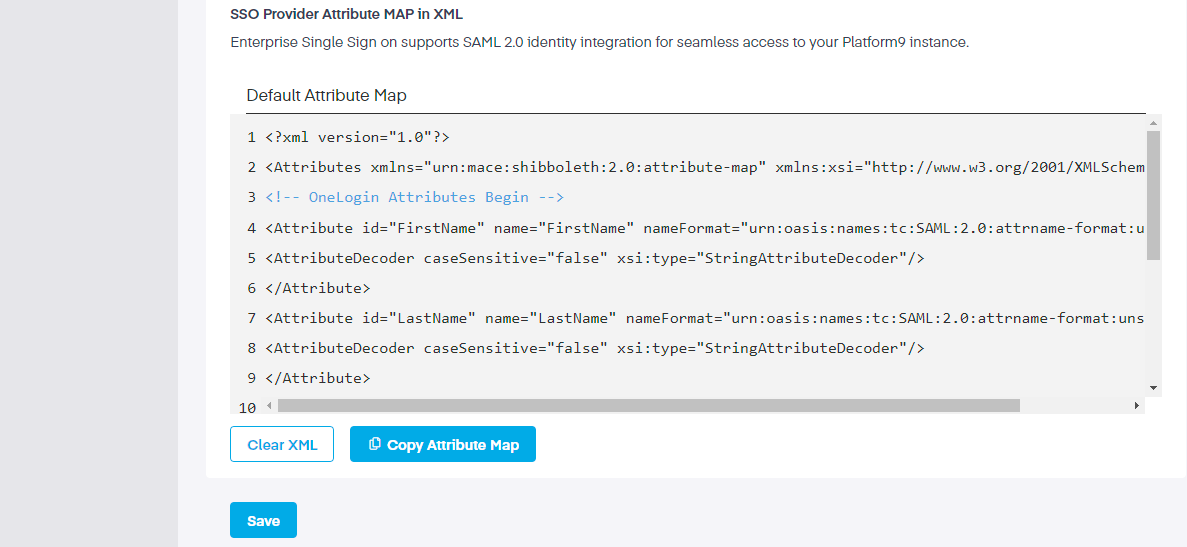
SAML
Security Assertion Markup Language (or SAML) is an open standard that lets users log into multiple sites using an identity or service providers to pass login information. There are two main types of SAML providers; service providers and identity providers.
Service providers get authentication from an identity provider that is used to grant authorization to the user. Identity providers perform the actual authentication that verifies the end user is who they say they are. It then sends that information to the service provider, along with the user’s access rights for the service.
SAML Groups
A SAML group allows an admin to define an attribute (or set of attributes) to better manage group permissions. These rule-based characteristics are mapped between a set of users and an external identity provider like SAML, LDAP, or AD to admin users into the Keystone identity service.
SSO integration relies on the 'Group' concept exposed by Keystone. A Keystone Group allows an Administrator to map a collection of users from his external identity provider (IDP) such as Okta to Platform9. When a user from that IDP signs into Platform9, and after authentication with the identity provider, Keystone identifies what Group the user belongs to based on the SAML attributes for this user supplied by the (IDP). The user's access to Tenants, Regions and the associated clusters are then decided based on that Group mapping.
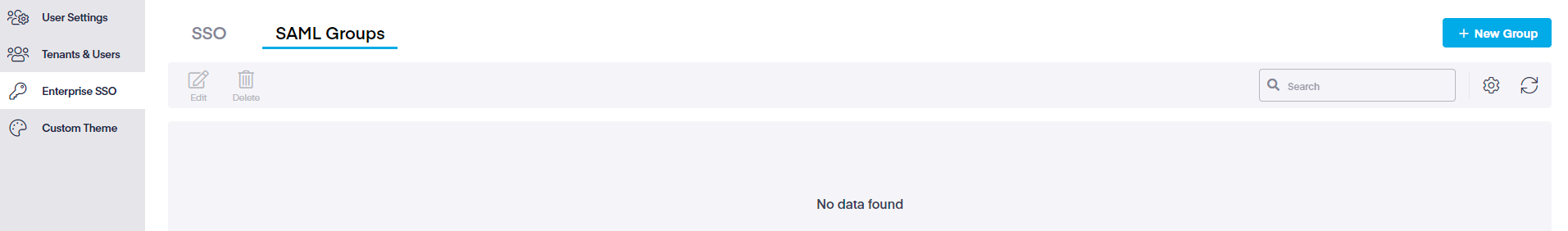
When the initial screen opens, no SAML groups will initially be seen. To create a group, click on the Add Group button in the top-right corner.
On the new page, enter the group name, description, and SAML attribute keys. If further attributes are required, click the + sign next to Add Group Mapping and add additional attributes and values as needed. Next, indicate which tenants this group can access, and the roles the users will be assigned within each tenant.
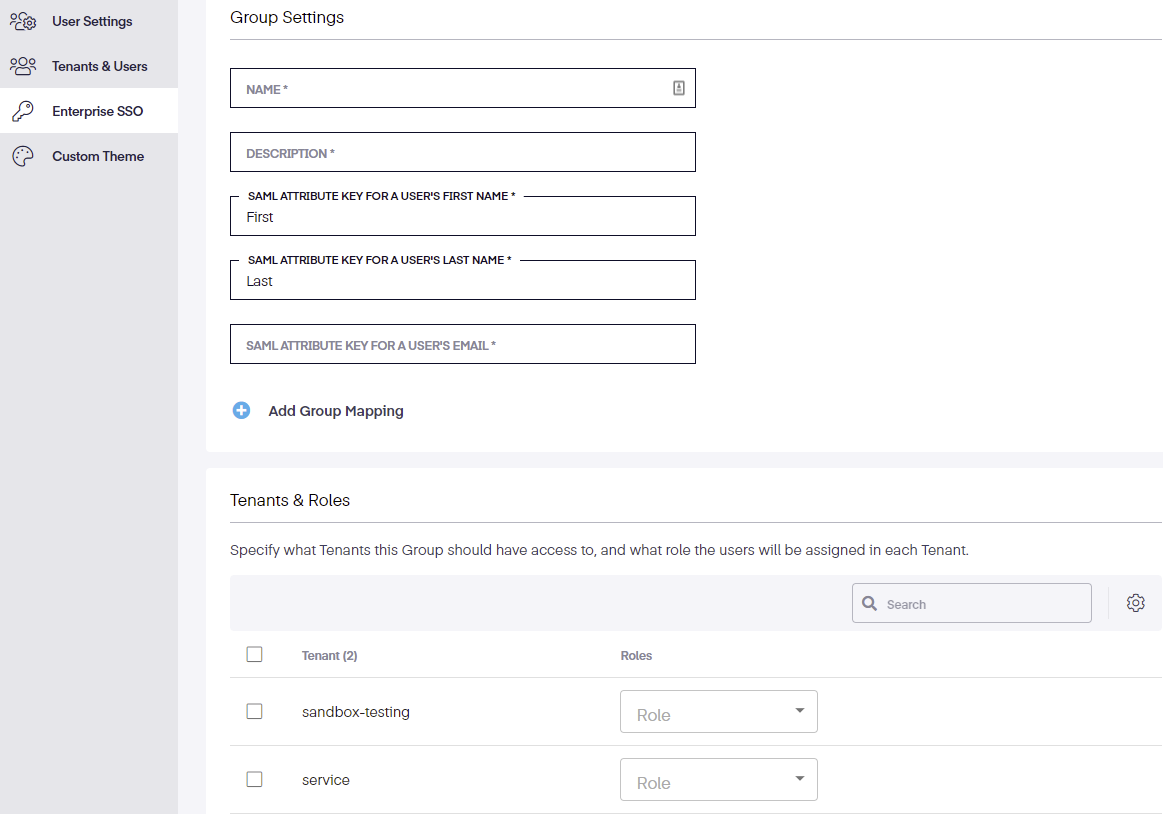
Admins should only assign a user to a unique group. If a user belongs to multiple groups, they will automatically be granted the privileges associated with each group.
If you have questions regarding this setup, reach out to our Support Team for further assistance.