PMK Release 5.5 Release Notes
The Platform9 Managed Kubernetes (PMK) version 5.5 release is now available with support for Kubernetes 1.21. The 5.5 release aims to bring multifold improvements to the User Experience with a brand new UI and App-Switching capability. This release adds brand new features and services including ECO, ArgoCD-as-a-Service, Metal3, and Catapult. This release continues to upscale Platform9's commitment to provide features with deep Kubernetes integration, built on Open-Source technologies.
All clusters running Kubernetes 1.19 must be upgraded prior to upgrading to PMK 5.5
Kubernetes 1.19 has reach End of Life as of 2021-10-28. New clusters should be built on 1.21.
Kubernetes 1.20 has been deprecated as of 2022-02-28. New clusters should be built on 1.21.
PMK Release Highlights
Catapult Remote Monitoring
As part of the Platform9 5.5 release we have made significant changes to our remote monitoring capabilities, introducing Kubernetes specific metrics and alerts that provide an additional layer of managed protection.
Every user of Platform9 now has access to monitoring that remotely monitors the critical functions of their Kubernetes clusters. The new remote monitoring is known as Catapult and has been built leveraging 100% open source Kubernetes Native tooling. Catapult monitoring monitors the following items within each cluster:
- etcd
- API Server
- Nodes
- Pods
- Calico networking
- Platform9 Managed Add-ons Health
- Platform9 Connectivity
By collecting key metrics Platform9 is able to provide alerts on events such as etcd backup failures, API Server client errors, Node availability, Node memory pressure, Pod crashloopbackoff and more.
Prometheus will now also run in agent mode on each node attached to PMK. This prometheus agent will scrape metrics from a number of targets and remote write these metrics on the Prometheus running in PMK SaaS Management Plane. The Alert Manager running in PMK SaaS Management Plane will send alerts to the customers.
In total there are 56 built-in alerts that can be configured to notify your team over email, webhook, Slack and ServiceNow.
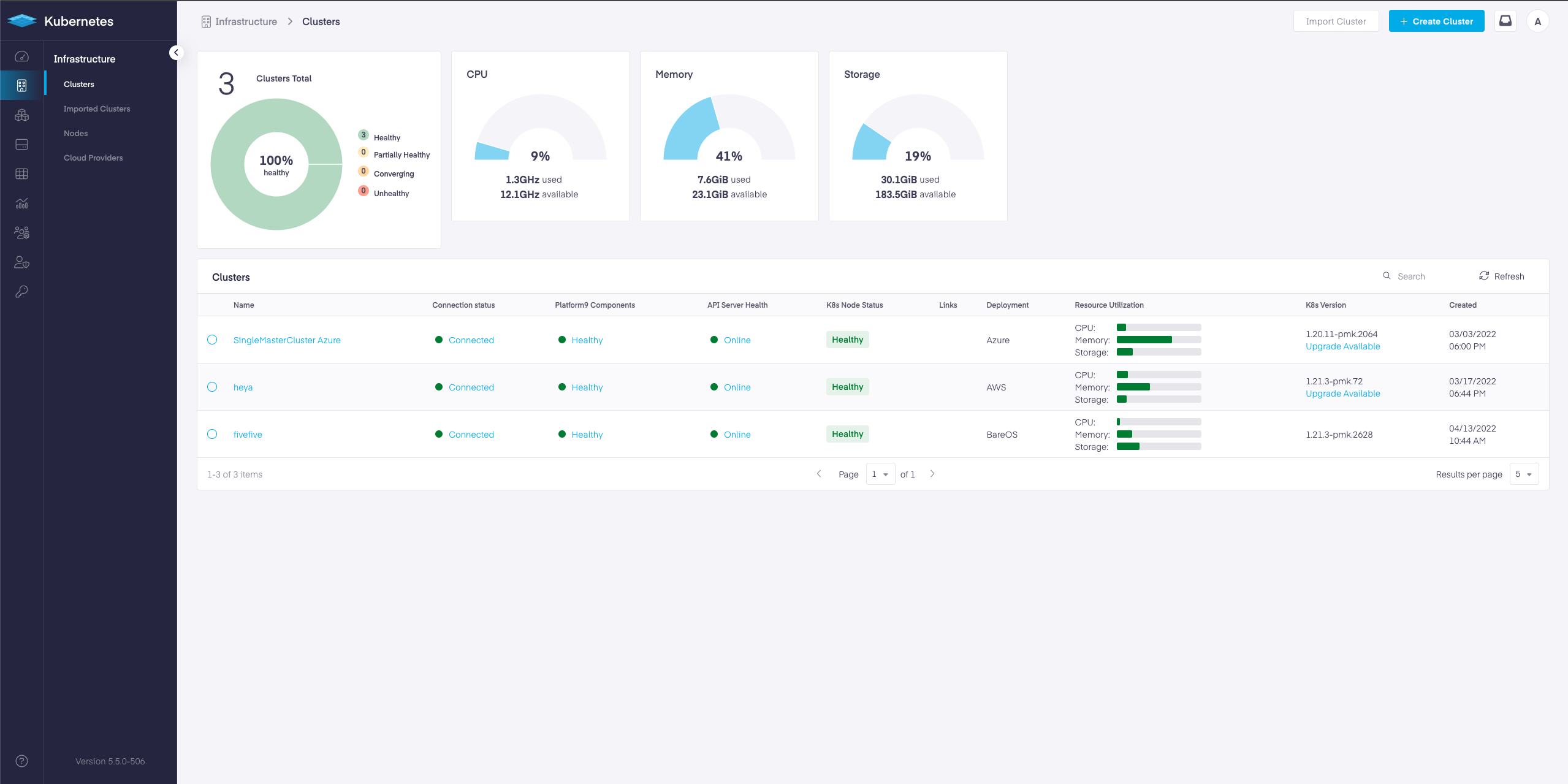
A remarkable new user experience.
PMK version 5.5 has a rebuilt WebApp that provides a significantly improved user experience. The following screenshots demonstrate various sections of the new user interface.
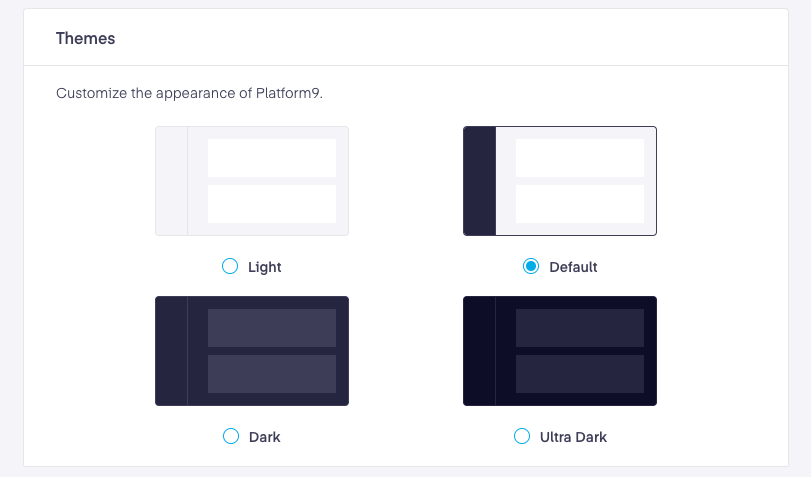
New Theming Capability
We added the ability to choose different themes to customize the appearance. Modifying the themes allow users to maximize productivity while enjoying an increased visual experience. These themes are divided into four main views.
- Light: The light theme is a clean looking motif that is very easy on the eyes and useful in brighter environments.
- Default: The default theme is not as bright as the light theme, but it is a low enough contrast to offset the lower contrast dark and ultra dark themes.
- Dark: Dark themes help reduce the brightness level cast by device screens, while meeting the minimal color contrast ratios needed to reduce eye strain. Adjusting the brightness down to a lower level better matches low light conditions. This facilitates improved screen usage in darker environments, which also conserves battery power.
- Ultra Dark: This theme uses an even darker color than the above dark theme, making it even easier on the eyes or excellent for a higher contrast option.
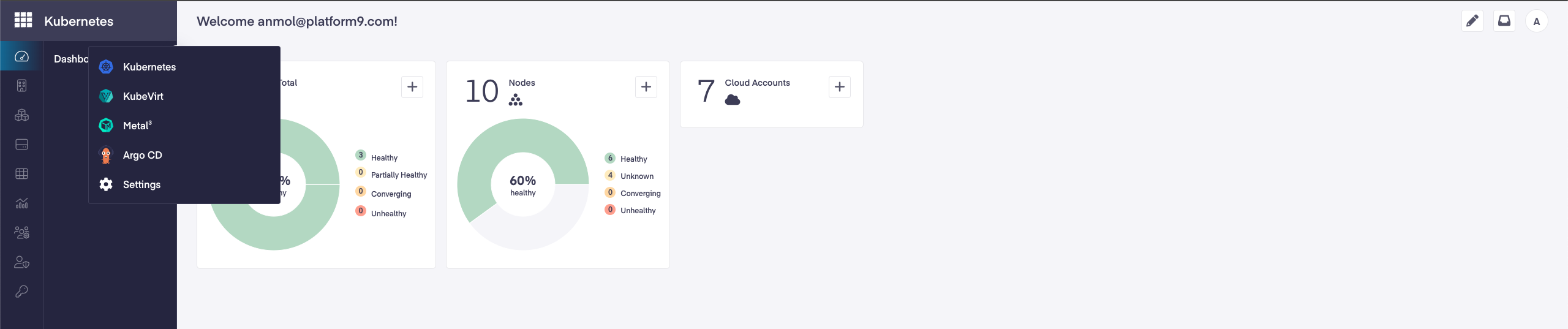
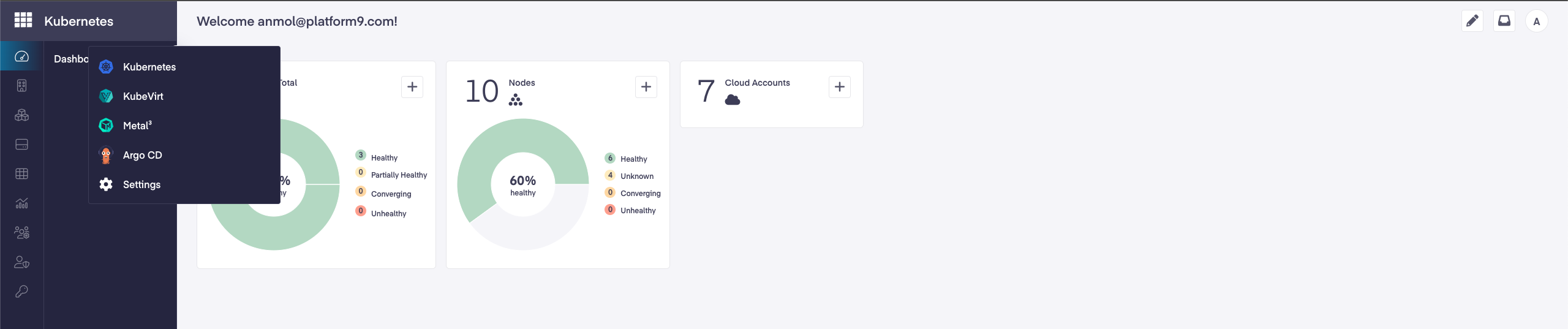
Application Switcher
With the arrival of PMK version 5.5, we have included a new App Switcher, which allows users the ability to maneuver seamlessly across the different services in the PMK UI.
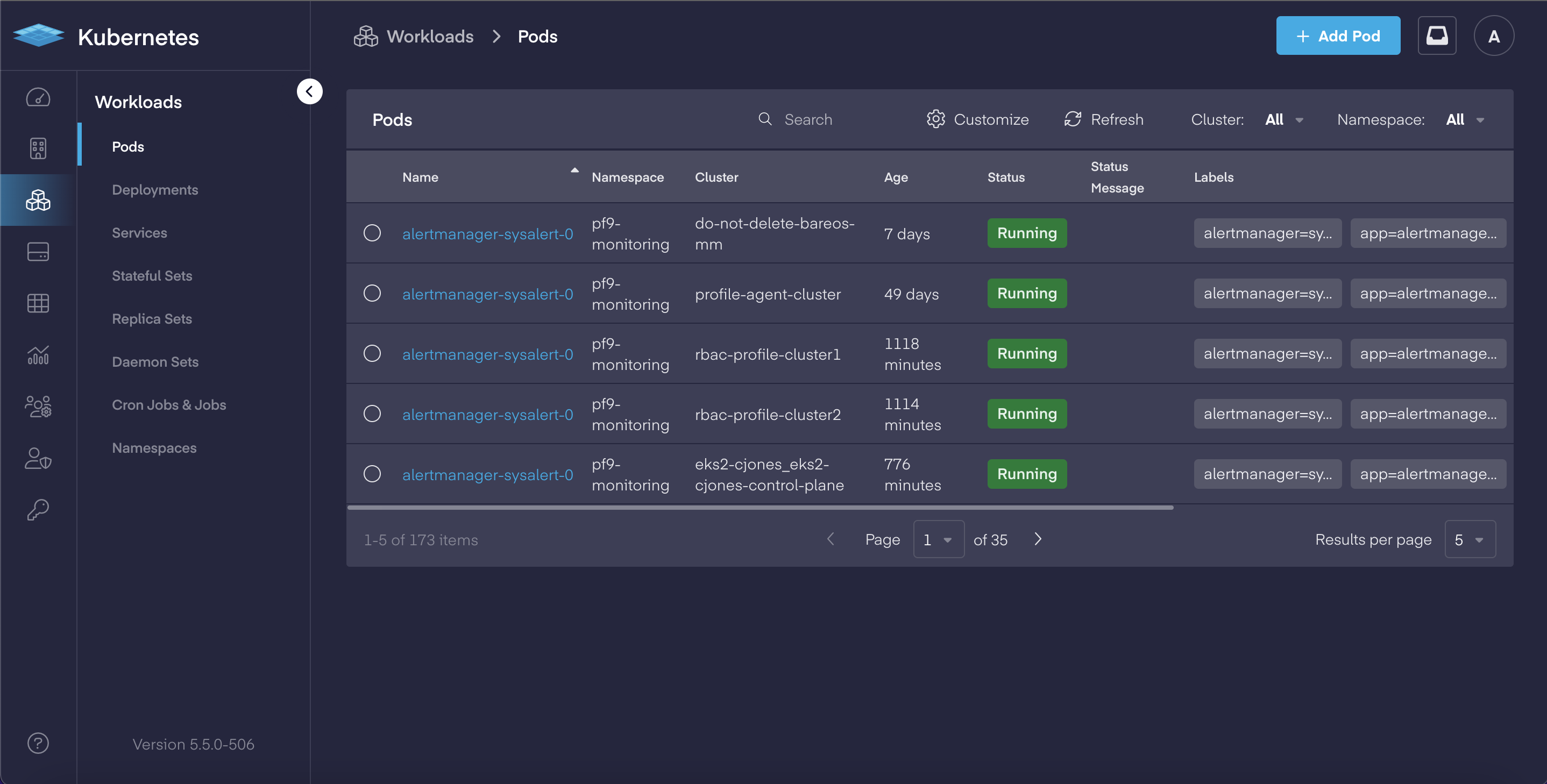
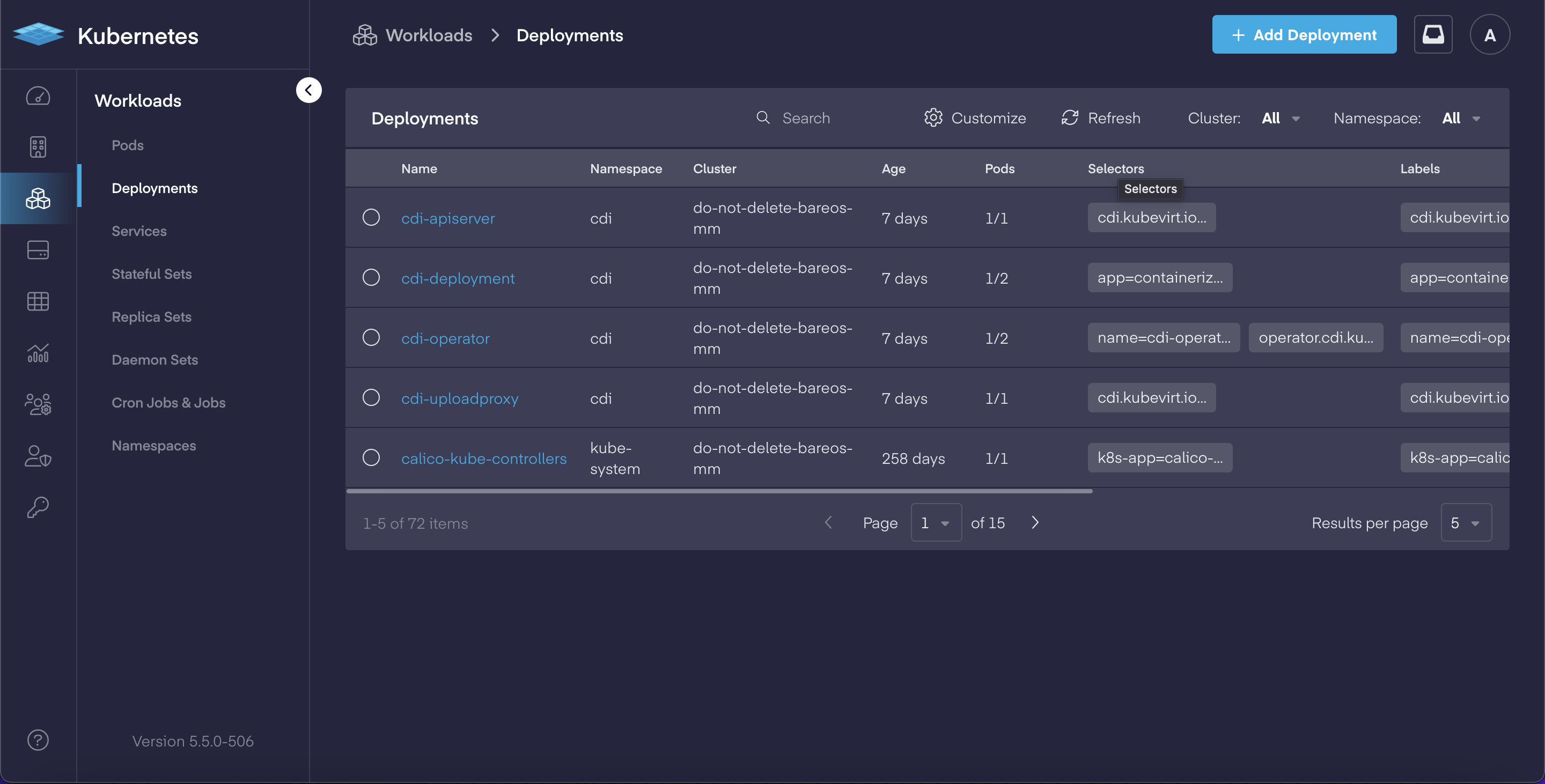
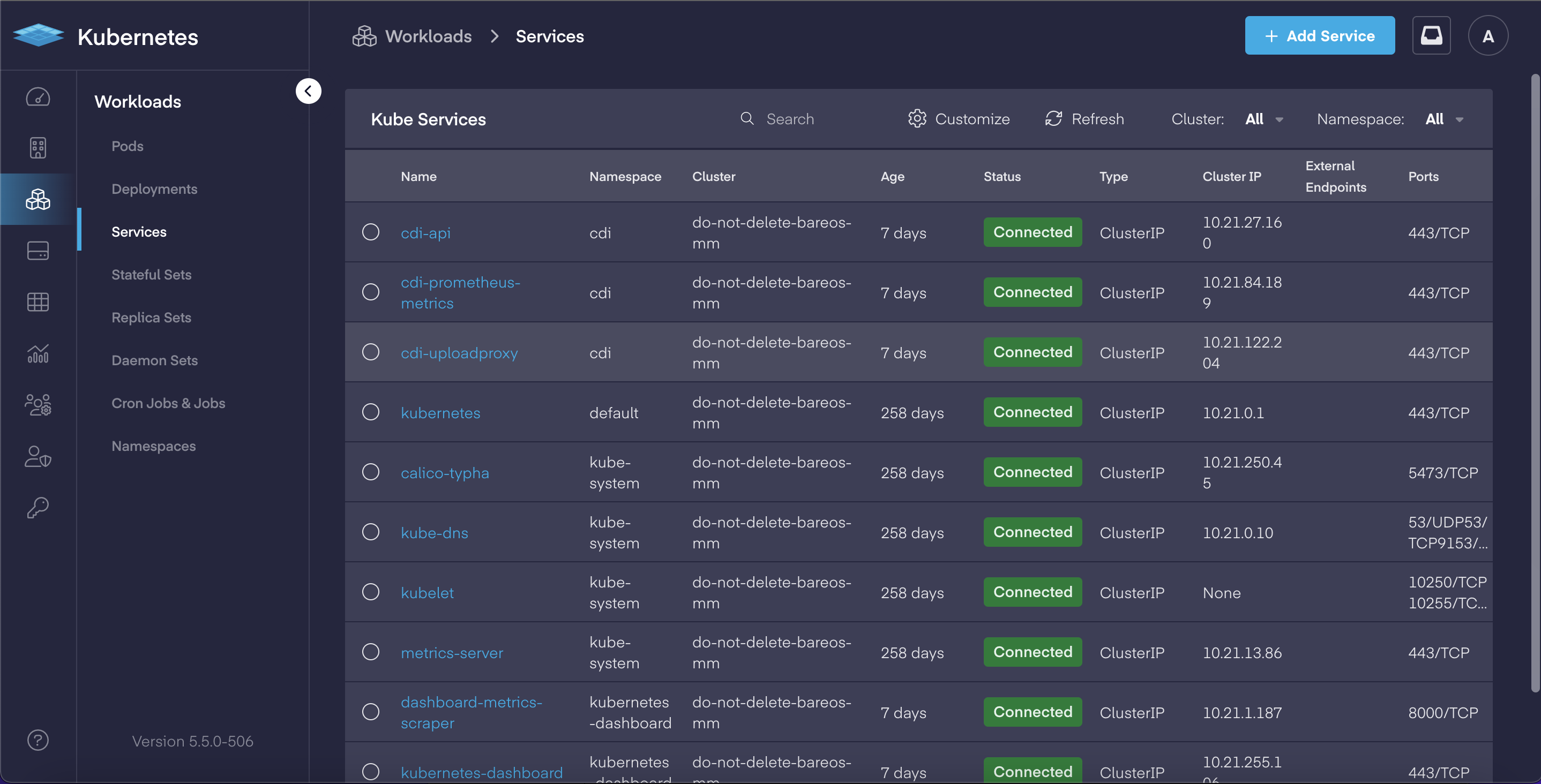
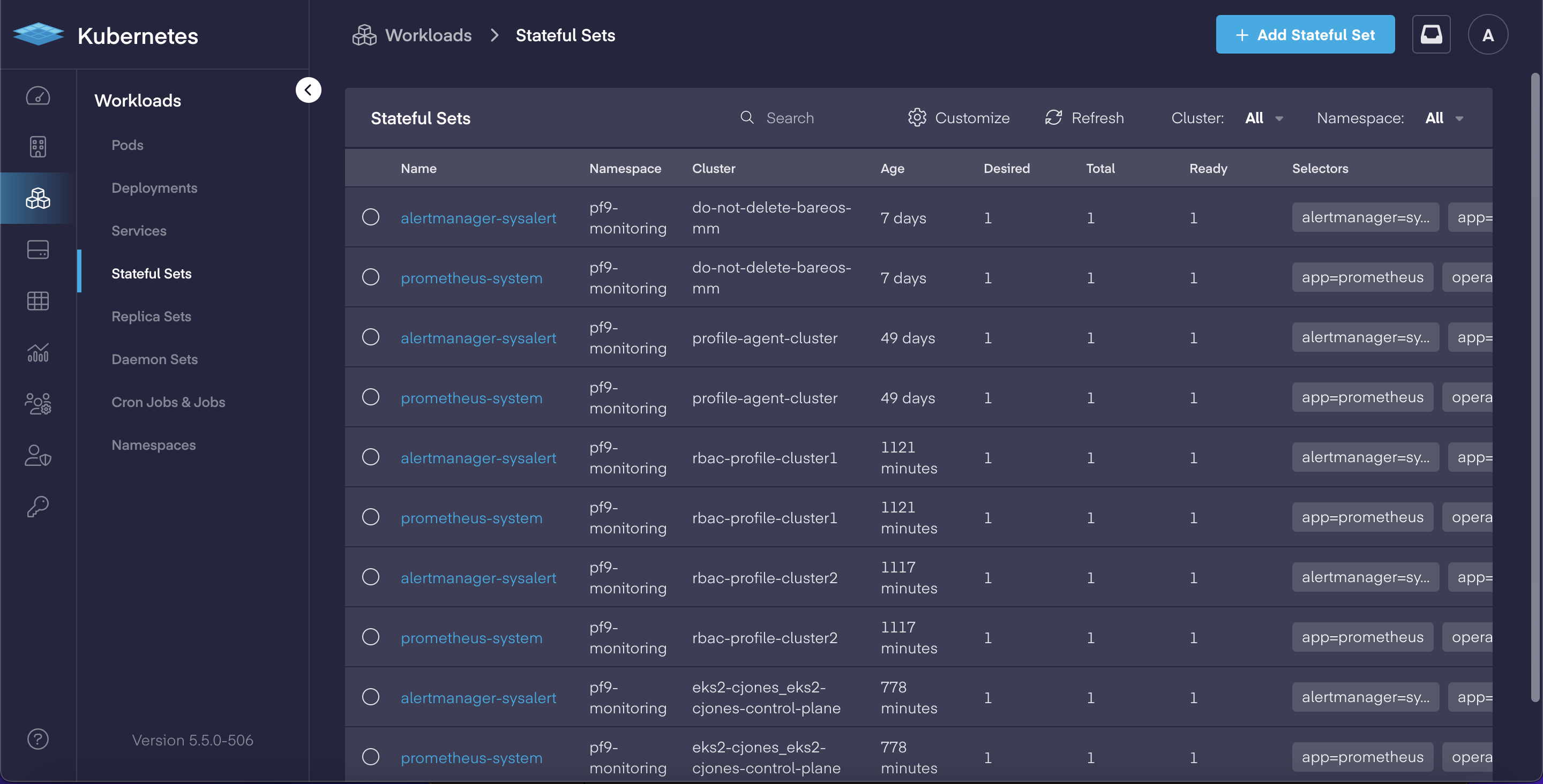
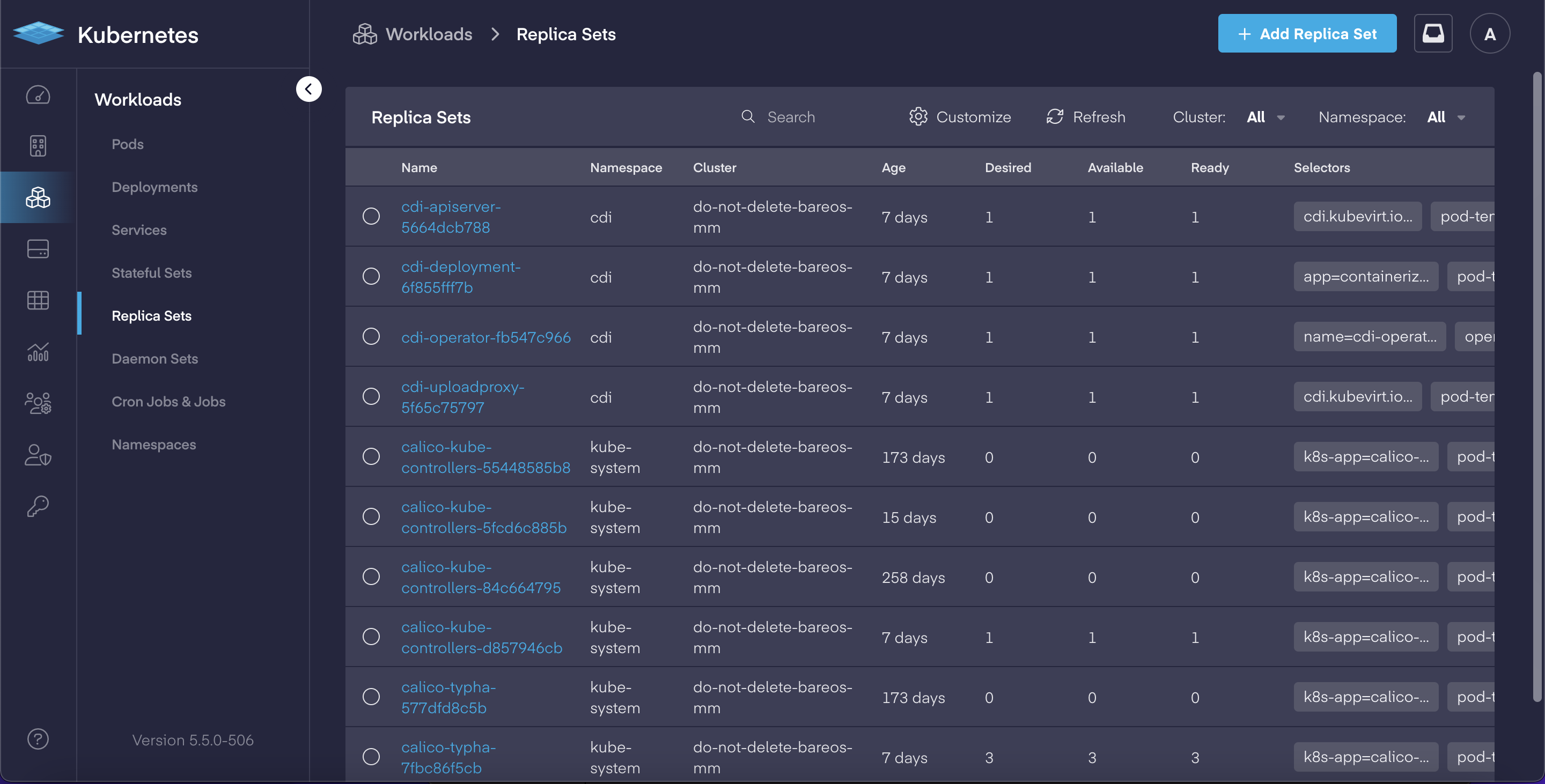
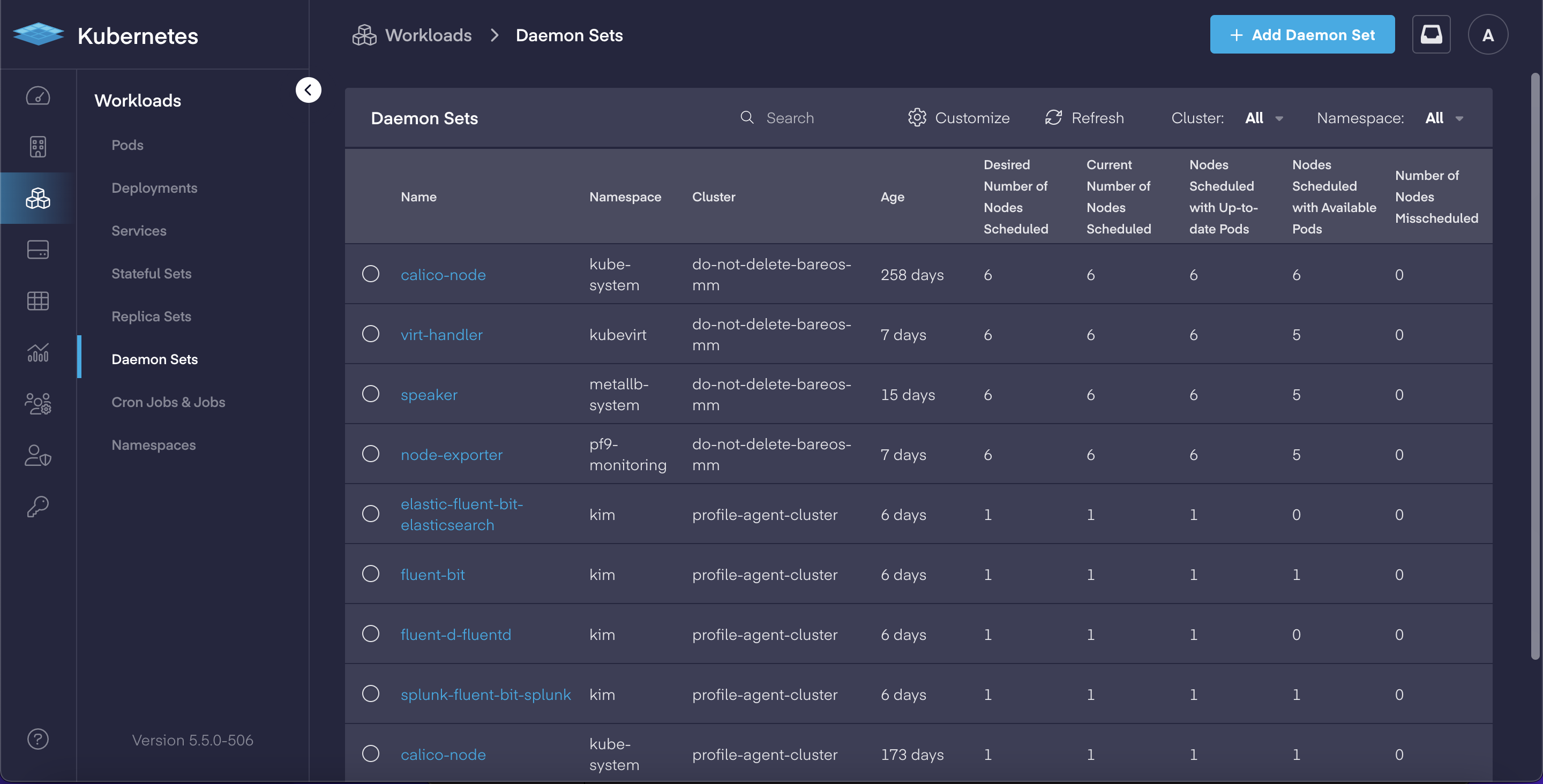
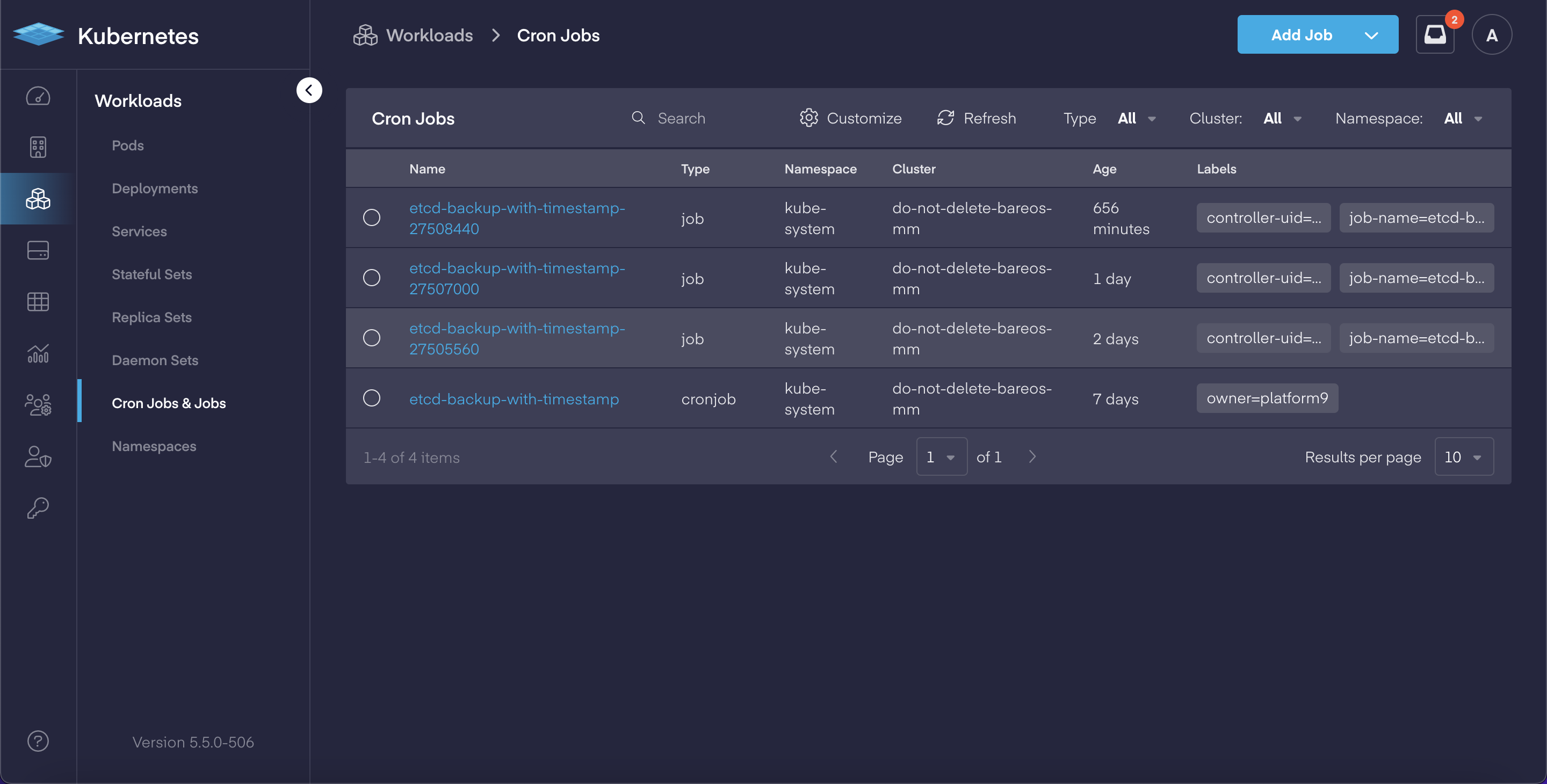
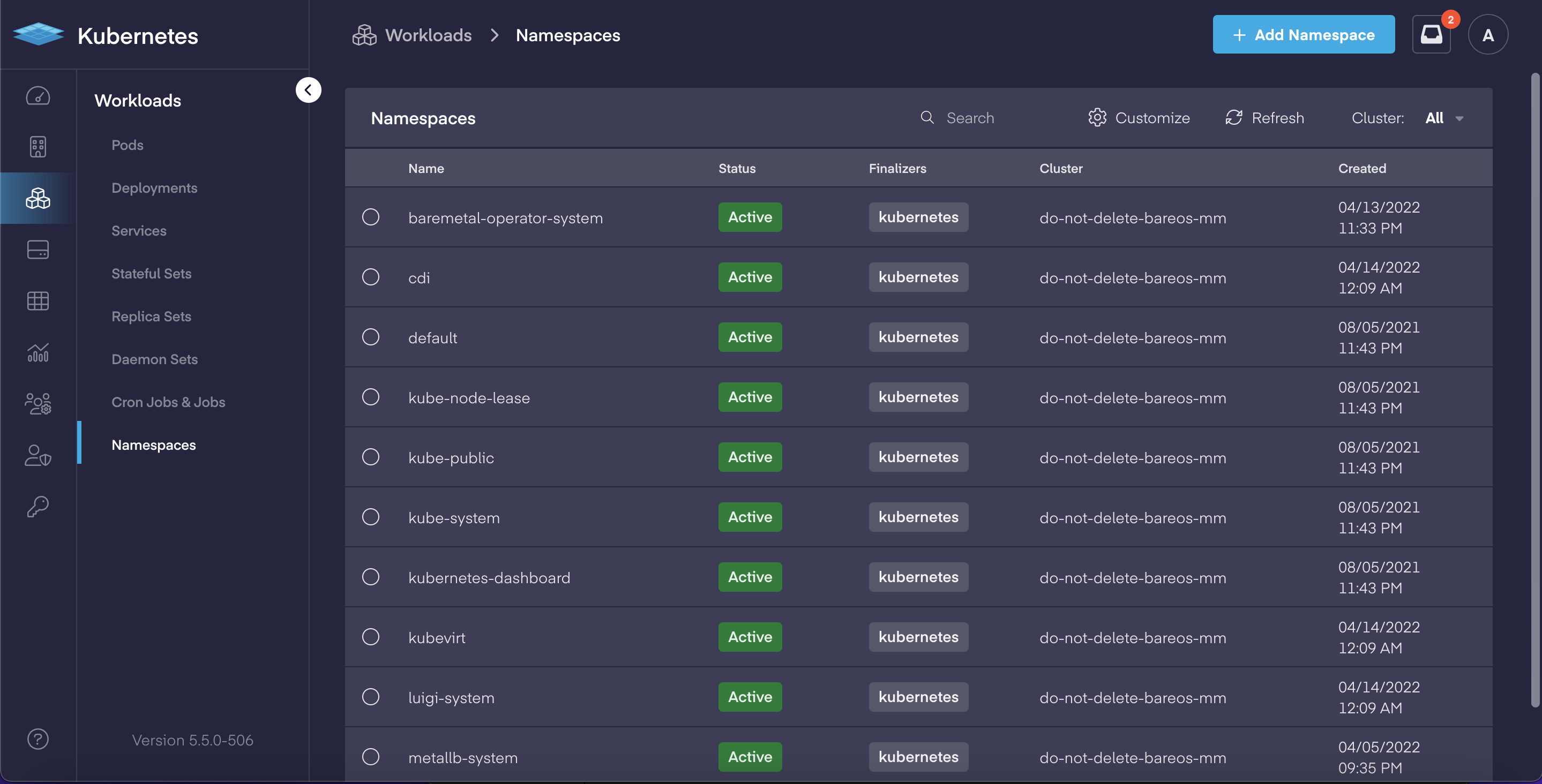
Deep-dive Cloud Native App Dashboards
In our continual effort to make Kubernetes easier to manage for both operators and developers, PMK 5.5 adds a complete set of deep-dive dashboards for working with cloud native applications. This includes: Pods, Deployments, Services, Stateful Sets, Replica Sets, Daemon Sets, Jobs & CronJobs sections now have dedicated views which allow users to:
- All resources are automatically linked to keep data in context
- Better visualize cluster configurations.
- Instantly access events and logs
Each in-depth dashboard provides the ability to review and quickly modify an object's YAML file for faster updates, and delivers the improved ability to troubleshoot issues.
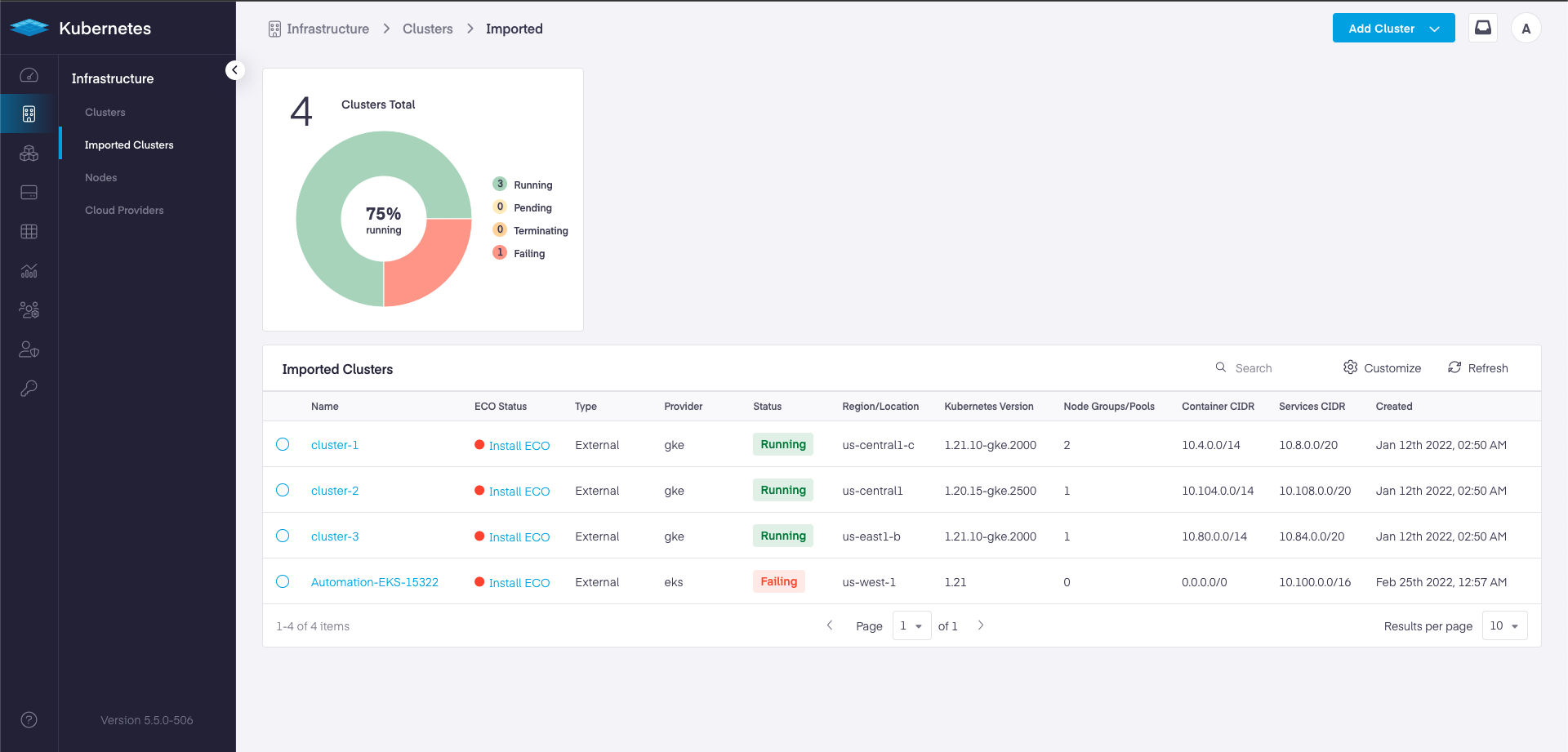
EKS, AKS and GKE Management using ECO
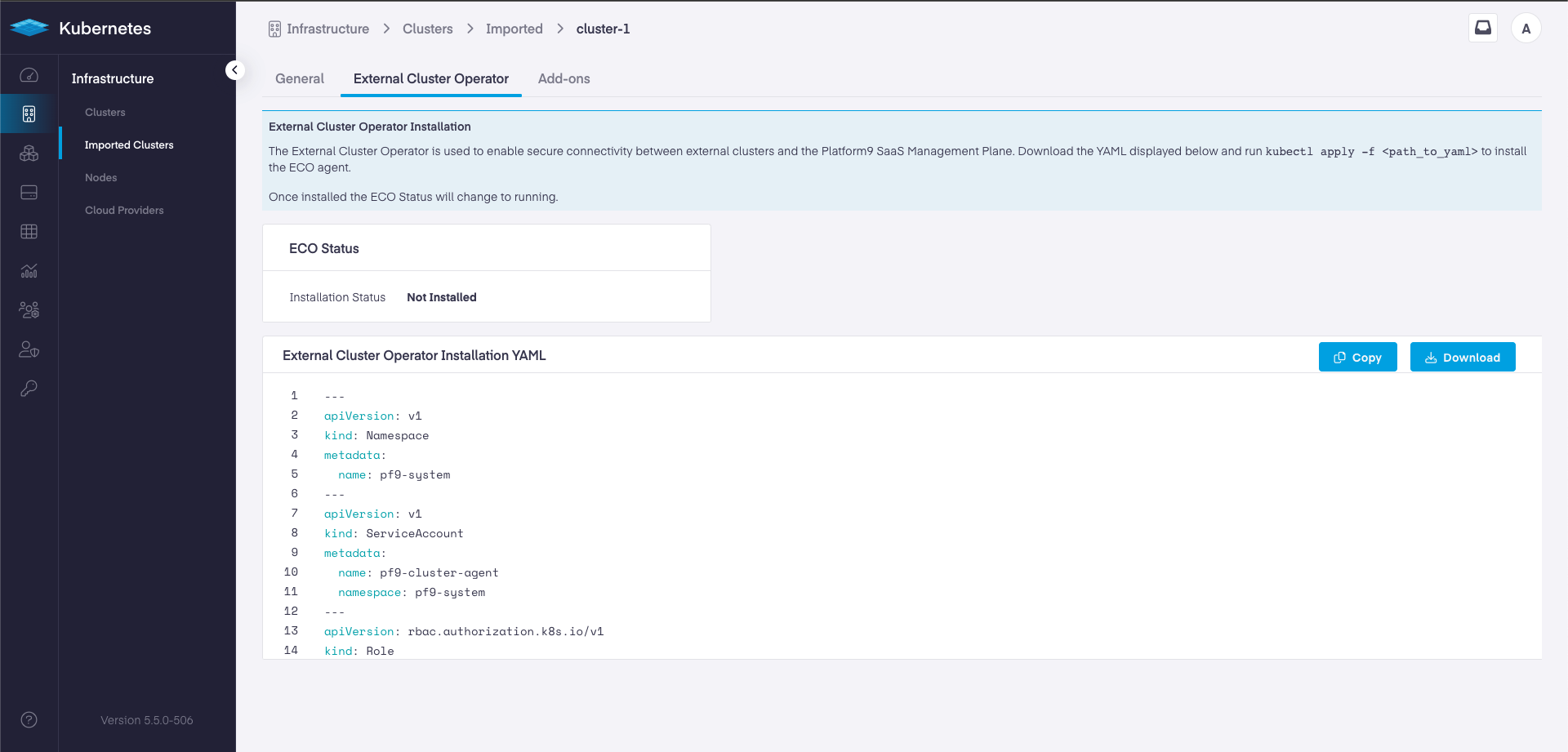
With 5.5 release we are enhancing our external cluster management with the introduction of the External Cluster Operator (ECO).
ECO is installed into EKS, AKS and GKE clusters, creating a secure outbound tunnel that connects the cluster to the SaaS Management Plane.
Once connected, ECO enables users to leverage Platform9 Managed Add-ons, such as in-cluster monitoring, deploy apps using ArgoCD to the Helm Service and quickly troubleshoot applications through the workload dashboards.
Platform9 CLI
The 1.14 pf9ctl release is now available and can be installed by running the following command.
bootstrap command
delete command
node commands
detach-nodeauthorize-nodedeauthorize-nodedecommission-node
--no-prompt flag to make pf9ctl more automation friendly.
ArgoCD as a Service [Early access]
Metal3
Platform9 Managed Bare Metal Release Notes
Enhancements & Updates
preventSinglePointFailure set to true by default, which ensures two CoreDNS replicas on a multi-node cluster.
Package Updates
The following packed components have been upgraded:
- calico: “v3.18.1”
- casaws: “1.14.8"
- casazure: “1.13.8”
- cni: “v0.9.0"
- coredns: “1.8.0”
- dashboard: “2.0.1"
- etcd: “v3.4.14”
- flannel: “v0.14.0"
- kubevirtaddon: “0.45.0"
- luigi: “0.3.0"
- metallb: “0.10.2”
- metricsserver: “0.5.0"
- monitoring: “0.46.0”
- profileagent: “2.0.0"
Please refer to the Managed Kubernetes Support Matrix for v5.5 to view all currently deployed or supported upstream component versions.
Known Issues
If an AWS Cloud Provider is configured to import clusters without the correct identity being added to the target cluster, Platform9 will be unable to access the cluster.
It's important to note that if you have used a Cloud Provider to register an EKS, AKS, or GKE cluster that was created with IAM user credentials, which no longer have access to the EKS, AKS, or GKE K8s clusters, Platform9 will fail with an 401 unauthorized error until that IAM user is given access to the K8s cluster.
View the EKS documentation here to ensure the correct access has been provisioned at for each imported cluster. https://aws.amazon.com/premiumsupport/knowledge-center/amazon-eks-cluster-access/
Current workaround is to delete /var/lib/docker manually.