Cloud Provider Checks
The pf9cp CLI helps users check IAM access and confirm pre-requisites for AWS, Azure and Google clouds. The CLI works by connecting to the target cloud using the same credentials as the Cloud Provider and validates if the credentials provided have the required access for Platform9 to build and manage clusters.
The pf9cp CLI supports Windows 10, MacOS, CentOS 7.X and Ubuntu 18.04 / 20.04
Install on Linux & macOS
From the command line of your machine, run the following to download and install the CLI tool.
$ bash <(curl -sL https://pmkft-assets.s3.us-west-1.amazonaws.com/IAM_Checker/pf9cp_setup)Successful installation should look like:
$ bash <(curl -sL https://pmkft-assets.s3.us-west-1.amazonaws.com/IAM_Checker/pf9cp_setup) ____ _ _ __ ___| _ \| | __ _| |_ / _| ___ _ __ _ __ ___ / _ \| |_) | |/ _` | __| |_ / _ \| '__| '_ ` _ \ (_) || __/| | (_| | |_| _| (_) | | | | | | | \__, ||_| |_|\__,_|\__|_| \___/|_| |_| |_| |_| /_/19:24:01:11 : Initializing: /Users/anmols/pf919:24:01:11 : Ensuring /Users/anmols/pf9/bin exists19:24:01:11 : Ensuring /Users/anmols/pf9/db exists19:24:01:11 : Ensuring /Users/anmols/pf9/log exists19:24:01:11 : Ensuring /Users/anmols/pf9/log/cli_install.log existsNote: SUDO access required to run Platform9 CLI. You might be prompted for your SUDO password.Downloading Platform9 CLI binary...Password:Platform9 CLI binary downloaded.Installing Platform9 CLI...19:24:09:11 : Platform9 CLI installation completed successfully.Platform9 CLI installation completed successfully !To start testing providers type: pf9cp helpInstall On Windows
Download the CLI from the below links depending on the configuration of your machine.
- For windows-32 : https://pmkft-assets.s3.us-west-1.amazonaws.com/IAM_Checker/pf9cp-win32.exe
- For windows-64 : https://pmkft-assets.s3.us-west-1.amazonaws.com/IAM_Checker/pf9cp-win64.exe
Make sure that the downloaded exe file is in a folder that's on the PATH environment variable.
- You can do this by either copying it into a folder that's already on the PATH or by adding your folder to the PATH.
- Example:
- Create a folder named pf9 in C drive.
- Copy the downloaded pf9cp-win64.exe to the C:\pf9 folder. Rename the file to pf9cp for convenience.
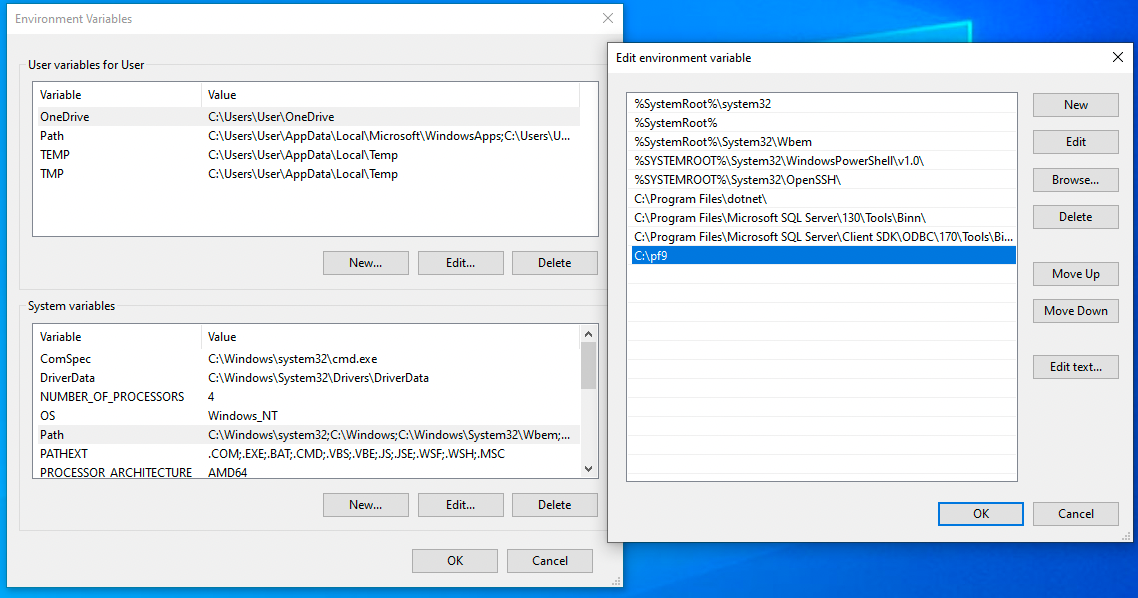
- Add C:\pf9 folder to your path by doing following:
- Type
Edit the system environment variables - Open the option
Edit the system environment variables - Click
Environment variables...button - Under
System Variablesbox find Path variable - Click
Edit - A window pops up, click
New - Type the C:\pf9 in it.
- Click
OKon all open windows and restart the command prompt to use it.
- Type
PF9CP CLI Commands
Command: help
This command provides help about supported commands.
$ pf9cp help CLI tool for Platform9 cloud provider checks.Usage: pf9cp [command]Available Commands: check-amazon-provider checks if user has amazon cloud permission check-azure-provider checks if user has azure cloud permission check-google-provider checks if user has google cloud permission help Help about any commandFlags: -h, --help help for pf9cp --verbose print verbose logsUse "pf9cp [command] --help" for more information about a command.Command: check-amazon-provider
This command checks if user has amazon cloud permissions.
$ pf9cp check-amazon-provider --helpChecks if user has the correct permissions to use the amazon cloud providerUsage: pf9cp check-amazon-provider [flags]Flags: -a, --access_key string sets the access key (required) -h, --help help for check-amazon-provider -i, --iam_user string sets the iam user (required) -r, --region string sets the region (default "us-east-1") -s, --secret_key string sets the secret key (required)Global Flags: --verbose print verbose logsFollow this link to get your AWS access key and secret key if you do not have them: https://docs.aws.amazon.com/powershell/latest/userguide/pstools-appendix-sign-up.html
Successful command run should look like:
$ pf9cp check-amazon-provider -i iamUser -a access-key -s secret-key -r us-east-1✓ ELB Access✓ Route53 Access✓ Availability Zones success✓ EC2 Access✓ VPC Access✓ IAM Access✓ Autoscaling Access✓ EKS AccessCommand: check-google-provider
This command checks if user has google cloud permissions.
$ pf9cp check-google-provider --helpChecks if service account has the correct roles to use the google cloud providerUsage: pf9cp check-google-provider [flags]Flags: -h, --help help for check-google-provider -n, --project_name string sets the project name (required) -e, --service_account_email string sets the service account email (required) -p, --service_account_path string sets the service account path (required)Global Flags: --verbose print verbose logsFollow this link to get your Google service account keys if you do not have them: https://cloud.google.com/iam/docs/creating-managing-service-account-keys
Successful command run should look like:
$ pf9cp check-google-provider -p /home/user/Downloads/service-account.json -n testProject -e user@email.com✓ Success roles/iam.serviceAccountUser✓ Failed roles/container.admin✓ Failed roles/compute.viewer✓ Success roles/viewerCommand: check-azure-provider
This command checks if user has azure cloud permissions
$ pf9cp check-azure-provider --helpChecks if service principal has the correct permissions to use the azure cloud providerUsage: pf9cp check-azure-provider [flags]Flags: -c, --client_id string sets the client(applicaiton) id (required) -h, --help help for check-azure-provider -k, --secret_key string sets the secret key (required) -s, --subscription_id string sets the ssubscription id (required) -t, --tenant_id string sets the tenant id (required)Global Flags: --verbose print verbose logsFollow this link to get your Azure tenant information if you do not have it: https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-how-to-find-tenant
Successful command run should look like:
$ pf9cp check-azure-provider -t tenantID -c clientID -s subscriptionID -k secretKey✓ Has access