Well Known Ports
The following ports are defined as the Ingress and Egress ports needed for a cluster. The following information is mainly geared directed towards running a cluster on OpenStack VMs, but it is equally applicable when running on baremetal or other Virtual Machine environments.
Ingress Rules
Keepalived
For the multi-master cluster, the openstack security group should allow traffic for VRRP protocol on the master nodes. To enable it, allow Ingress to multicast address 224.0.0.18/32, IP Protocol: 112
TCP ports
In an Openstack environment with port security enabled, Calico should be running with IPinIP enabled and NATOutgoing set to true. Set the following firewall (security group) rules

Note:
- These security group rules were tested with cluster nodes in a 10.128.146.0/23 subnet.
- The ICMP rule can be ignored.
- For On-Prem version, SSH port 22 should be allowed from the Deployment Host.
- Port 2379 is only used on the localhost by etcd in PMK, so it was not opened in the Security group.
- For kubelet, port 10250 was found to be sufficient.
- The cAdvisor port 4194 was not opened.
Additionally, Calico (IPinIP Always and NATOutgoing=True) requires port 179 and 5473 to be open.
One can therefore open ports mentioned in the PMK Networking Prerequisites article and additionally, ports 179, 5473 required by Calico.
In addition to above rules, additional rules can be created to allow specific application ingress traffic.
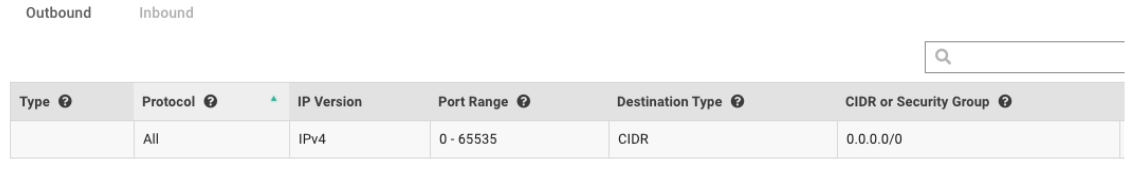
Egress Rules
Everything outgoing is allowed as part of the egress rule. This also allows Egress to multicast address 224.0.0.18/32, IP Protocol: 112 required for keepalived.
BareMetal environments
When Calico IPinIP mode and NATOutgoing are enabled, the firewall rules for BareMetal hosts are the same as the ones for the openstack environment. When Calico IPinIP mode is set to Never, create additional rules to allow ingress traffic from the containersCidr & servicesCidr.
- IP spoofing checks are expected to be disabled to bootstrap a cluster with Calico IPinIP set to ‘Never’ and NATOutgoing set to false.
- The IPinIP and NATOutgoing settings go hand in hand.
Ingress Rules
For On-Prem, air gapped clusters, the management plane host requires access to SSH into the cluster nodes.
Egress Rules
All nodes need port 443 outgoing allowed to the management plane’s IP address to communicate with the deployment unit (DU). Note that the DU and management plane are one and the same thing.